Crook's Millions: Targeting Executive Office 365 Accounts
Table of Contents
The Allure of Executive Office 365 Accounts
Executive Office 365 accounts are incredibly attractive to cybercriminals due to several factors:
-
High-value targets: Executives possess access to sensitive financial information, including bank details, investment strategies, and merger & acquisition plans. They also control strategic plans, confidential contracts, intellectual property, and crucial company data. Compromising their accounts yields significant financial gains and provides attackers with a massive competitive advantage.
-
Privileged access: Executive accounts often have elevated permissions within the Office 365 environment. This means that a successful breach can allow attackers to access and modify data across the entire organization, potentially crippling operations and causing widespread damage. This privileged access allows for lateral movement throughout the network.
-
Data breaches: Stolen data from executive accounts can lead to significant financial losses, irreparable reputational damage, hefty legal liabilities, and serious regulatory penalties, potentially resulting in millions of dollars in fines and remediation costs.
-
Real-world examples: Numerous high-profile breaches have targeted executive accounts, resulting in significant data leaks and financial losses. The 2017 Equifax breach, for instance, exposed sensitive personal data due to a compromised executive account. These real-world examples underscore the critical need for robust security measures.
Tactics Employed by Cybercriminals
Cybercriminals employ a range of sophisticated tactics to target executive Office 365 accounts:
Phishing and Spear Phishing
-
Sophisticated emails: Attackers craft highly convincing emails mimicking legitimate communications from trusted sources, often personalized to the specific executive. These emails may contain urgent requests, seemingly important notifications, or even fabricated internal memos.
-
Social engineering: These attacks leverage social engineering principles to manipulate users into revealing their credentials or clicking on malicious links. They often exploit urgency and trust to pressure the recipient into acting quickly without thinking critically.
-
Advanced techniques: Cybercriminals utilize advanced techniques such as lookalike domains (e.g., microsoftt.com instead of microsoft.com) and email spoofing to make their messages appear authentic.
Credential Stuffing and Brute-Force Attacks
-
Credential reuse: Attackers use stolen credentials from other breaches (obtained through data leaks on the dark web) to attempt logins to Office 365 accounts. This technique leverages the common practice of reusing passwords across multiple accounts.
-
Automated attacks: Brute-force attacks use automated tools to try numerous password combinations until a successful login is achieved. These attacks are particularly effective against accounts with weak or easily guessable passwords.
-
MFA is crucial: The importance of strong, unique passwords and multi-factor authentication (MFA) cannot be overstated in mitigating these risks. MFA adds an extra layer of security that significantly increases the difficulty of successful login attempts.
Malware and Ransomware
-
Malicious software: Malware can be installed on devices via phishing emails or infected attachments, allowing attackers to steal credentials and data directly from the executive's computer.
-
Ransomware attacks: Ransomware encrypts critical data, rendering it inaccessible, and demands a ransom for decryption. This can cripple an organization's operations and lead to significant financial losses.
-
Endpoint security: Robust endpoint security solutions, including antivirus software, firewalls, and intrusion detection systems, are crucial to prevent malware infections and ransomware attacks. Regular software updates are also essential.
Exploiting Vulnerabilities
-
Software flaws: Attackers actively search for and exploit known security flaws in Office 365 applications and their integrations. These vulnerabilities can provide entry points for malicious actors.
-
Vulnerability scanning: Regular vulnerability scanning and patching are vital to identify and address security flaws before they can be exploited. Staying up-to-date with security patches from Microsoft is paramount.
Protecting Executive Office 365 Accounts
Protecting executive Office 365 accounts requires a multi-layered approach:
Multi-Factor Authentication (MFA)
MFA is the single most effective way to significantly reduce the risk of unauthorized access. It requires users to provide multiple forms of authentication, such as a password and a code from a mobile app, making it exponentially harder for attackers to gain access even if they obtain a password.
Strong Password Policies
Enforce strong, unique passwords for all accounts. Consider using a password manager to help generate and securely store complex passwords. Regular password changes should also be a part of security protocols.
Security Awareness Training
Educate employees, particularly executives, about phishing scams, social engineering tactics, and best practices for safe online behavior. Regular training sessions and simulated phishing campaigns can significantly improve awareness and reduce susceptibility.
Advanced Threat Protection
Invest in advanced threat protection tools like Microsoft Defender for Office 365. These solutions provide enhanced protection against sophisticated phishing attacks, malware, and other threats.
Regular Security Audits and Penetration Testing
Proactive security assessments, including regular security audits and penetration testing, are crucial for identifying and addressing vulnerabilities before attackers can exploit them. These assessments should simulate real-world attacks to highlight weaknesses in the security posture.
Conclusion
The "crook's millions" are a very real threat to organizations with vulnerable executive Office 365 accounts. By understanding the tactics employed by cybercriminals and implementing robust security measures, organizations can significantly reduce their risk. Investing in strong security practices, including MFA, security awareness training, and advanced threat protection, is not just a cost; it's an investment in protecting sensitive data and preventing costly breaches. Don't become another statistic – proactively protect your executive Office 365 accounts and prevent the theft of your "crook's millions." Take action today to secure your organization’s most valuable asset.

Featured Posts
-
 Manfaatkan Cangkang Telur Pupuk Alami Untuk Tanaman Dan Pakan Hewan
May 03, 2025
Manfaatkan Cangkang Telur Pupuk Alami Untuk Tanaman Dan Pakan Hewan
May 03, 2025 -
 Ukraine Farages Zelenskyy Comments Spark Outrage
May 03, 2025
Ukraine Farages Zelenskyy Comments Spark Outrage
May 03, 2025 -
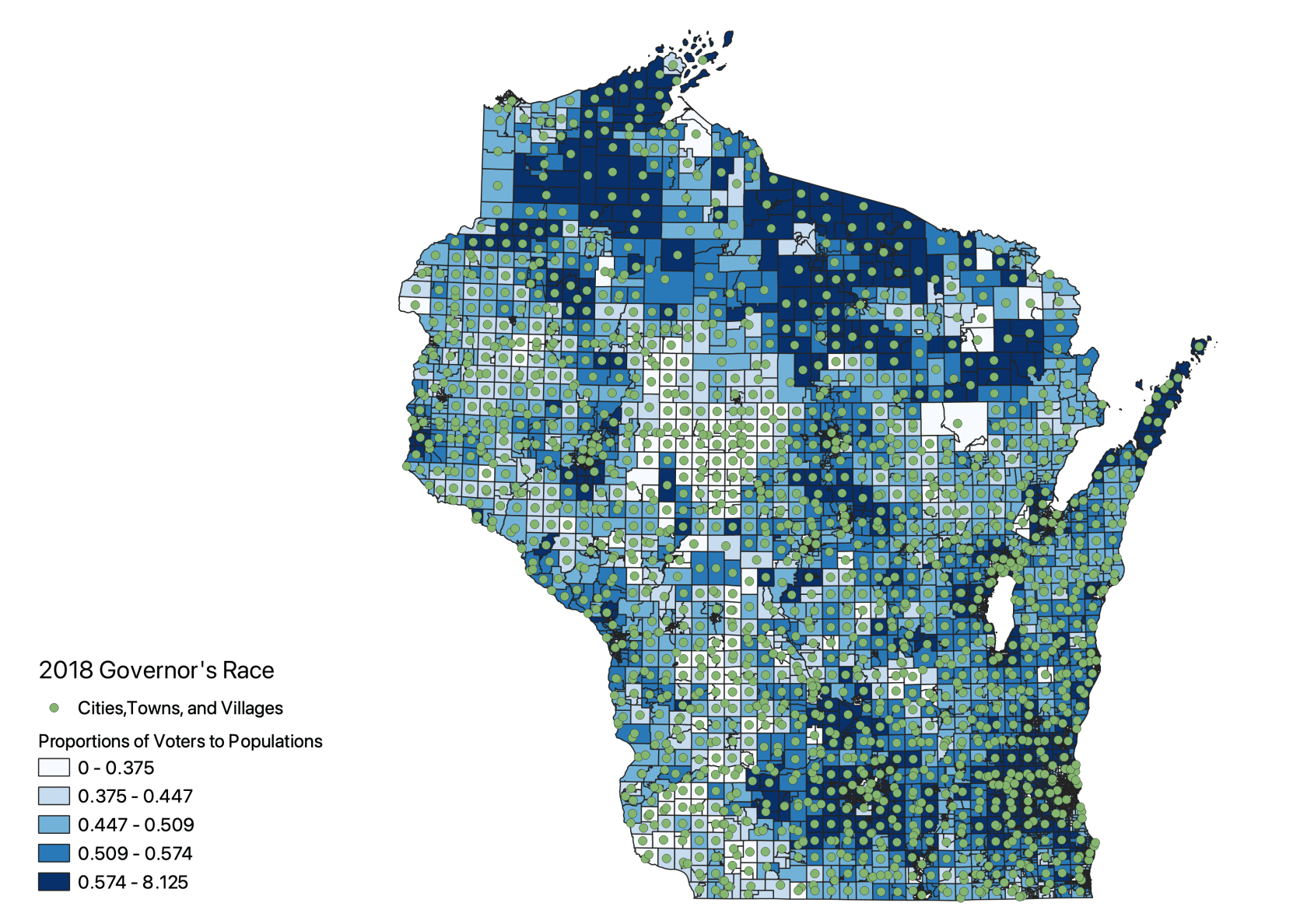 Analyzing Voter Turnout In Florida And Wisconsin Understanding The Political Landscape
May 03, 2025
Analyzing Voter Turnout In Florida And Wisconsin Understanding The Political Landscape
May 03, 2025 -
 Fortnites V34 30 Update New Content Sabrina Carpenter And Gameplay Changes
May 03, 2025
Fortnites V34 30 Update New Content Sabrina Carpenter And Gameplay Changes
May 03, 2025 -
 Belgium Vs England Live Tv Channel Kick Off Time And Streaming Guide
May 03, 2025
Belgium Vs England Live Tv Channel Kick Off Time And Streaming Guide
May 03, 2025
Latest Posts
-
 The Future Of Reform Uk Five Reasons For Worry
May 03, 2025
The Future Of Reform Uk Five Reasons For Worry
May 03, 2025 -
 Why Reform Uk Is In Deep Trouble Five Crucial Factors
May 03, 2025
Why Reform Uk Is In Deep Trouble Five Crucial Factors
May 03, 2025 -
 Five Reasons Why Reform Uk Could Fail
May 03, 2025
Five Reasons Why Reform Uk Could Fail
May 03, 2025 -
 Reform Uks Survival In Question Five Critical Issues
May 03, 2025
Reform Uks Survival In Question Five Critical Issues
May 03, 2025 -
 Understanding Reform Uks Political Impact Farages Influence
May 03, 2025
Understanding Reform Uks Political Impact Farages Influence
May 03, 2025
