Crook's Office365 Hacking Scheme Nets Millions, Say Federal Authorities
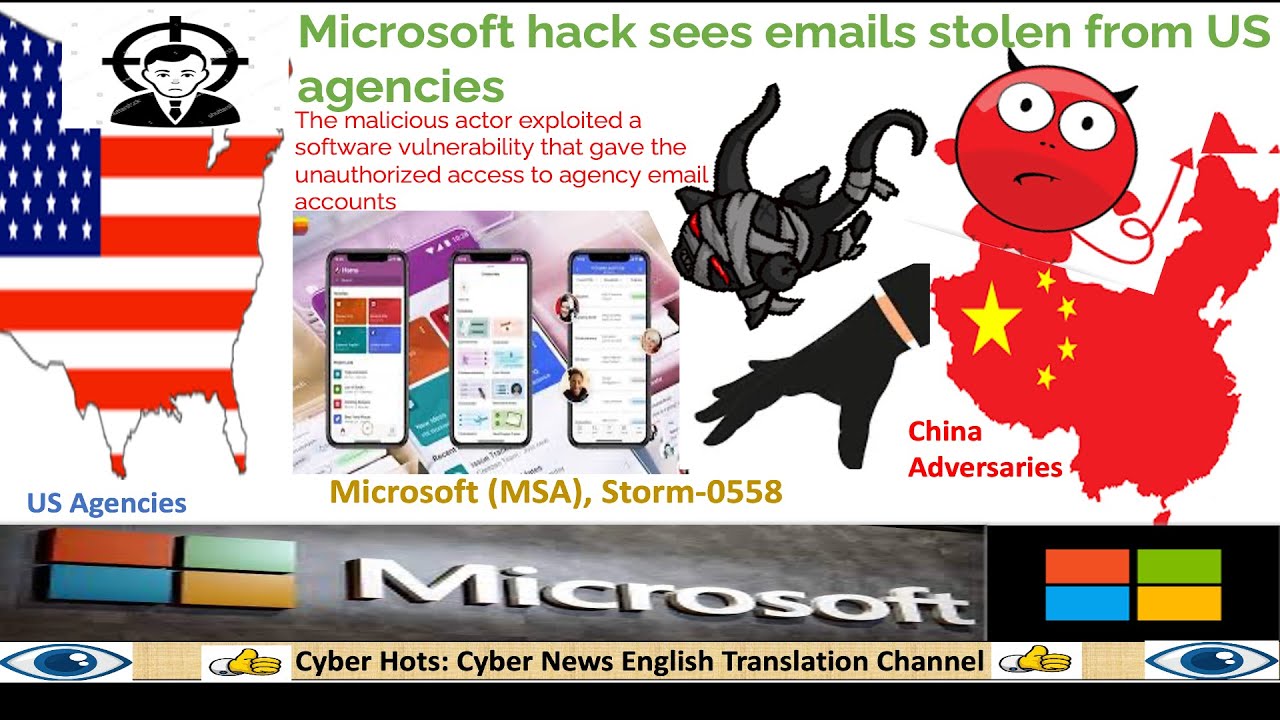
Table of Contents
The Mechanics of the Office365 Hacking Scheme
This Office365 security breach utilized a multi-pronged approach, leveraging various techniques to gain unauthorized access to victim accounts. The criminals employed a combination of sophisticated phishing campaigns, exploiting known vulnerabilities, and potentially using stolen credentials obtained from other sources. This layered approach allowed them to bypass many standard security measures.
- Specific examples of phishing emails used: The phishing emails often mimicked legitimate communications from trusted sources, using subject lines like "Urgent: Invoice Payment Required," or "Your Office365 Account Needs Verification." The emails contained malicious links leading to cleverly disguised phishing websites designed to steal login credentials.
- Vulnerabilities exploited: While specific vulnerabilities haven't been publicly disclosed to prevent further exploitation, it's likely that the hackers targeted known weaknesses in older versions of Office365 software or leveraged vulnerabilities in third-party applications integrated with the platform.
- Techniques for gaining access to Office365 accounts: The hackers likely employed credential stuffing, using lists of stolen usernames and passwords obtained from other breaches to attempt logins on Office365 accounts. Brute-force attacks, systematically trying various password combinations, were also a likely tactic. This Microsoft 365 compromise demonstrates the importance of robust password management practices.
Who Were the Victims of This Office365 Hack?
The Office365 hacking scheme targeted a diverse range of organizations and individuals, demonstrating the indiscriminate nature of this type of cybercrime. While the full scope of the victims remains unclear, early reports suggest a broad impact.
- Examples of industries affected: The attackers seemingly targeted various sectors, including financial services, healthcare, and small to medium-sized businesses (SMBs). This highlights the fact that no industry is immune to these types of attacks.
- Geographic location of affected organizations or individuals: The geographic reach of the attack is currently under investigation, but it's suspected that victims are spread across multiple countries. This highlights the global nature of cybercrime.
- Size of organizations targeted: The attack affected both large enterprises and smaller businesses, indicating that scale wasn't a primary factor in target selection. This underscores the importance of robust cybersecurity measures for organizations of all sizes.
The Financial Impact of the Office365 Breach
The financial consequences of this Office365 breach are staggering. The total amount of money stolen is estimated to be in the millions of dollars. This represents a significant financial loss for the affected businesses and individuals.
- Total amount of money stolen: Precise figures are still emerging, but early estimates place the total losses in the multi-million dollar range.
- Financial impact on individual victims or organizations: Many smaller businesses facing this type of business email compromise (BEC) have reported severe financial strain, some even facing closure due to the losses.
- Indirect costs: Beyond the direct financial losses from theft, victims face substantial indirect costs, including legal fees, costs associated with data recovery, and reputational damage, leading to a significant overall economic impact. These hidden costs often exceed the initial financial losses from the ransomware attacks or data breach itself.
Law Enforcement Response to the Office365 Hacking Scheme
Federal authorities are actively investigating this Office365 hacking scheme and have initiated a comprehensive cybercrime investigation.
- Details about the investigation: The investigation involves collaboration between multiple agencies and international partners to track down the perpetrators and disrupt their operations.
- Arrests made (if any): At the time of writing, information regarding arrests is limited, but the investigation is ongoing.
- Charges filed: Charges related to computer fraud and abuse, identity theft, and conspiracy are expected to follow as the investigation progresses.
Protecting Your Organization from Office365 Hacks
Protecting your organization from similar Office365 hacks requires a multi-layered approach focusing on prevention and detection.
- Implementing multi-factor authentication (MFA): MFA adds an extra layer of security, significantly reducing the risk of unauthorized access, even if credentials are compromised.
- Regular security awareness training for employees: Educate employees about phishing tactics and social engineering techniques to avoid falling victim to these attacks.
- Keeping software updated and patched: Regularly update Office365 and all related software to patch known vulnerabilities.
- Using strong, unique passwords: Encourage employees to use strong, unique passwords for all accounts, utilizing password managers if necessary.
- Implementing robust email security solutions: Utilize advanced email security solutions that can detect and filter out phishing emails and malicious attachments before they reach users' inboxes.
Conclusion
This Office365 hacking scheme underscores the critical need for robust cybersecurity measures. The attackers employed a sophisticated approach, targeting a wide range of victims and resulting in significant financial losses. Law enforcement is actively pursuing the perpetrators, but proactive measures are crucial for organizations to protect themselves. Don't become the next victim of an Office365 hacking scheme. Implement strong Office365 security measures today—including multi-factor authentication, regular security awareness training, and robust email security solutions—to protect your organization from devastating financial and reputational damage. Prioritize Office365 protection and ensure your data remains secure.

Featured Posts
-
 This Weeks Must Hear Albums Ezra Furman Billy Nomates And Damiano David
May 18, 2025
This Weeks Must Hear Albums Ezra Furman Billy Nomates And Damiano David
May 18, 2025 -
 Damiano Davids Next Summer Where To Stream
May 18, 2025
Damiano Davids Next Summer Where To Stream
May 18, 2025 -
 Netflixs Top 10 A True Crime Docuseries Unexpected Victory
May 18, 2025
Netflixs Top 10 A True Crime Docuseries Unexpected Victory
May 18, 2025 -
 11 Inmates Escape New Orleans Jail Sheriff Confirms Murder Suspects Among Fugitives
May 18, 2025
11 Inmates Escape New Orleans Jail Sheriff Confirms Murder Suspects Among Fugitives
May 18, 2025 -
 Netflix Docuseries Captures 9 11 Survivors Fight For Life
May 18, 2025
Netflix Docuseries Captures 9 11 Survivors Fight For Life
May 18, 2025
Latest Posts
-
 Southwest Washingtons Economic Future Navigating The Tariff Challenge
May 18, 2025
Southwest Washingtons Economic Future Navigating The Tariff Challenge
May 18, 2025 -
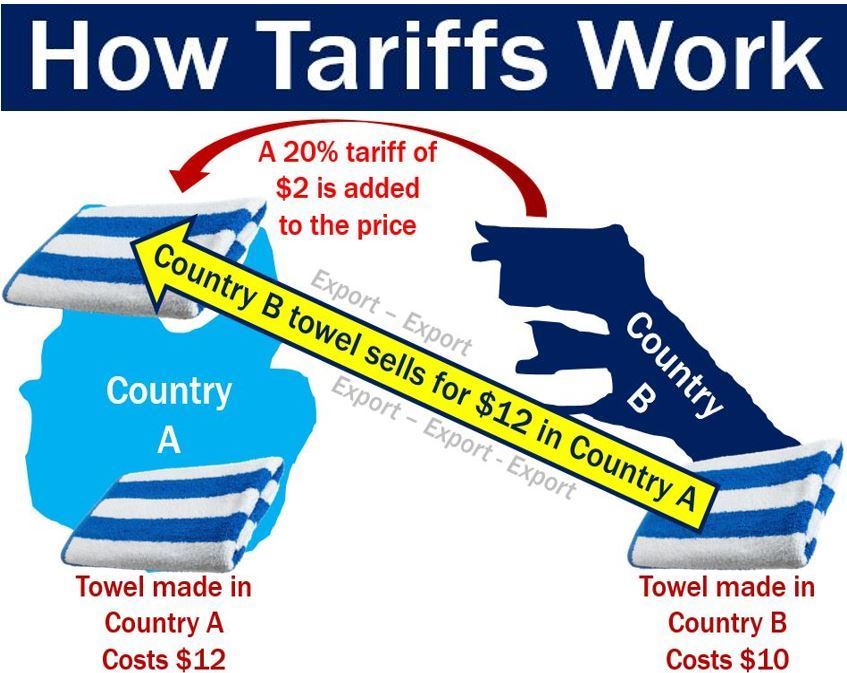 The Impact Of Tariffs On Southwest Washingtons Economy
May 18, 2025
The Impact Of Tariffs On Southwest Washingtons Economy
May 18, 2025 -
 Tariffs Hit Southwest Washington Businesses Brace For Impact
May 18, 2025
Tariffs Hit Southwest Washington Businesses Brace For Impact
May 18, 2025 -
 Analyzing The Financial Success Of Major Music Festivals
May 18, 2025
Analyzing The Financial Success Of Major Music Festivals
May 18, 2025 -
 Economic Benefits Of Large Scale Music Events A Case Study
May 18, 2025
Economic Benefits Of Large Scale Music Events A Case Study
May 18, 2025
