Cybercriminal Accused Of Millions In Executive Office365 Data Theft

Table of Contents
The Accused and the Modus Operandi
While the identity of the accused remains partially obscured pending legal proceedings, information gleaned from investigations points towards a sophisticated operation.
Identity of the Accused (if known):
At this stage, details regarding the accused's identity are limited to protect the ongoing investigation and to avoid jeopardizing the legal process. However, law enforcement agencies involved suggest a high level of technical expertise and likely involvement in organized cybercrime. Further details will be released as the case progresses and information is declassified.
The Method of Data Theft:
The alleged cybercriminal gained access to executive Office365 accounts through a multi-pronged approach, exploiting several vulnerabilities:
- Sophisticated Phishing Campaigns: The attacker allegedly employed highly targeted phishing attacks, focusing on executive assistants with access to key accounts. These emails mimicked legitimate communications, containing malicious links or attachments designed to deliver malware.
- Exploitation of Weak Security Settings: Investigations suggest that vulnerabilities in the target organizations' Office365 security configurations were exploited. This included inadequate password policies, a lack of multi-factor authentication, and insufficient employee training on cybersecurity best practices.
- Credential Stuffing and Brute-Force Attacks: Attempts to gain access through credential stuffing (using previously compromised credentials from other breaches) and brute-force attacks (trying numerous password combinations) were also reportedly detected.
- Use of Malware and Advanced Persistent Threats (APTs): Once initial access was gained, malware was likely deployed to maintain persistent access to the network and exfiltrate data over extended periods.
Bullet Points: Key steps in the alleged Office365 data theft included:
- Compromised login credentials through phishing emails.
- Exploitation of API vulnerabilities within the Office365 ecosystem.
- Data exfiltration via cloud storage services and encrypted channels.
- Use of advanced techniques to evade detection and maintain persistent access.
The Scale of the Data Breach and its Impact
The alleged Office365 data theft represents a significant incident with far-reaching consequences.
Types of Data Stolen:
The stolen data allegedly included an extensive range of highly sensitive information:
- Financial records, including bank statements and investment details.
- Confidential intellectual property, including product designs and strategic plans.
- Customer data, encompassing personally identifiable information (PII) such as names, addresses, and contact details.
- Internal communications, including emails and documents containing sensitive business strategies and negotiations.
Financial Losses and Reputational Damage:
The financial losses resulting from this Office365 data theft are estimated to be in the millions of dollars. Beyond the direct financial impact, the affected organizations are facing significant reputational damage, potential legal repercussions, and the cost of remediation and recovery. The breach could also lead to regulatory fines under data protection laws like GDPR and CCPA.
Bullet Points: Consequences of the data breach:
- Millions of dollars in financial losses due to fraud, data recovery, and legal costs.
- Severe damage to company reputation, leading to loss of customer trust and market share.
- Potential legal repercussions, including lawsuits from affected individuals and regulatory fines.
- Significant disruption to business operations during the investigation and recovery process.
Lessons Learned and Cybersecurity Best Practices
This case underscores the critical need for robust cybersecurity measures to protect against Office365 data theft and other cyber threats.
Strengthening Office 365 Security:
Organizations must prioritize enhancing their Office365 security posture through several key strategies:
- Mandatory Multi-Factor Authentication (MFA): Implement MFA for all user accounts to significantly increase security.
- Regular Security Audits and Penetration Testing: Conduct regular assessments to identify vulnerabilities and weaknesses in your systems.
- Comprehensive Employee Security Awareness Training: Educate employees about phishing scams, social engineering tactics, and secure password practices.
- Robust Password Policies and Management: Enforce strong password policies, including password complexity requirements and regular password changes.
- Data Loss Prevention (DLP) Measures: Implement DLP tools to monitor and prevent sensitive data from leaving your organization's network.
Responding to a Data Breach:
In the event of a data breach, swift and decisive action is crucial:
- Immediately contain the breach to limit further damage and data exfiltration.
- Notify affected individuals and regulatory bodies as required by law.
- Conduct a thorough forensic investigation to determine the extent of the breach and identify the root cause.
- Implement remediation measures to address vulnerabilities and prevent future attacks.
Bullet Points: Key cybersecurity best practices to prevent Office365 data theft:
- Regular software updates and patching to address security vulnerabilities.
- Strong password management practices, including password managers and MFA.
- Implementation of firewalls and intrusion detection systems to monitor network traffic.
- Regular security awareness training for employees to combat phishing and social engineering attacks.
Conclusion
The alleged cybercriminal's access to millions of dollars worth of data through executive Office365 accounts serves as a stark warning about the ever-evolving threat landscape. This case highlights the significant financial and reputational consequences of Office365 data theft. The scale of the breach and the methods employed underscore the need for proactive and comprehensive cybersecurity strategies. Don't become the next victim of Office365 data theft. Implement robust security measures today – including multi-factor authentication, regular security audits, and employee training – to safeguard your valuable data and protect your organization's future. Proactive defense against Office365 data theft is not just a best practice, it's a business imperative.

Featured Posts
-
 Mnaqshat Hywyt Hwl Alabtkar Fy Tb Alhyat Alshyt Almdydt Bmntda Abwzby
Apr 28, 2025
Mnaqshat Hywyt Hwl Alabtkar Fy Tb Alhyat Alshyt Almdydt Bmntda Abwzby
Apr 28, 2025 -
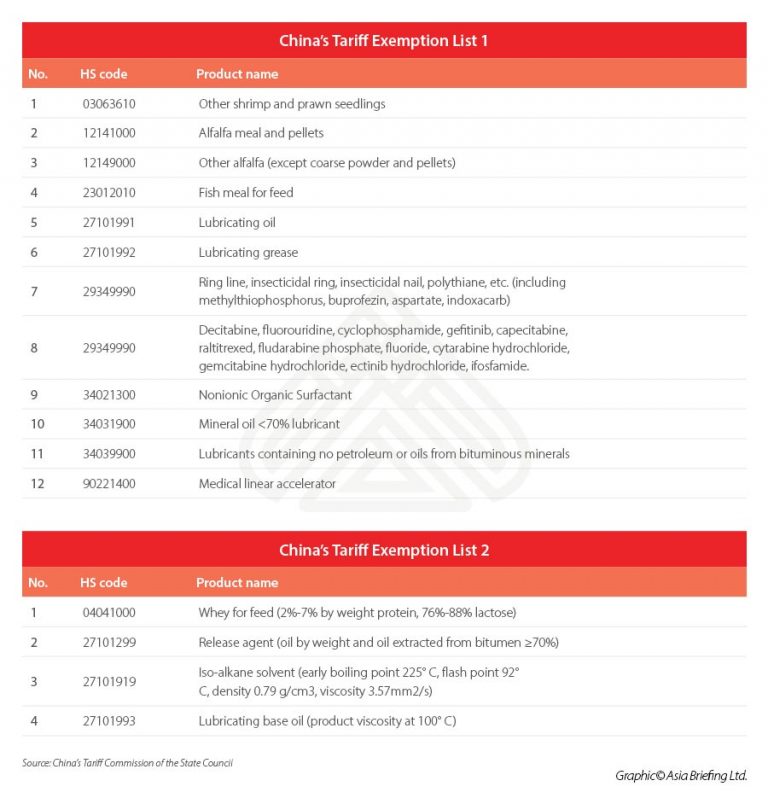 Understanding Chinas Selective Tariff Exemptions For Us Products
Apr 28, 2025
Understanding Chinas Selective Tariff Exemptions For Us Products
Apr 28, 2025 -
 Abwzby Tstdyf Mntda Rayda Llabtkar Fy Tb Alhyat Alshyt Almdydt
Apr 28, 2025
Abwzby Tstdyf Mntda Rayda Llabtkar Fy Tb Alhyat Alshyt Almdydt
Apr 28, 2025 -
 Merd Fn Abwzby Kl Ma Thtaj Merfth En Antlaqth Fy 19 Nwfmbr
Apr 28, 2025
Merd Fn Abwzby Kl Ma Thtaj Merfth En Antlaqth Fy 19 Nwfmbr
Apr 28, 2025 -
 Red Sox Lineup Adjustment Coras Game 1 Strategy
Apr 28, 2025
Red Sox Lineup Adjustment Coras Game 1 Strategy
Apr 28, 2025
