Executive Office365 Accounts Breached: Millions Stolen In Sophisticated Hacking Scheme

Table of Contents
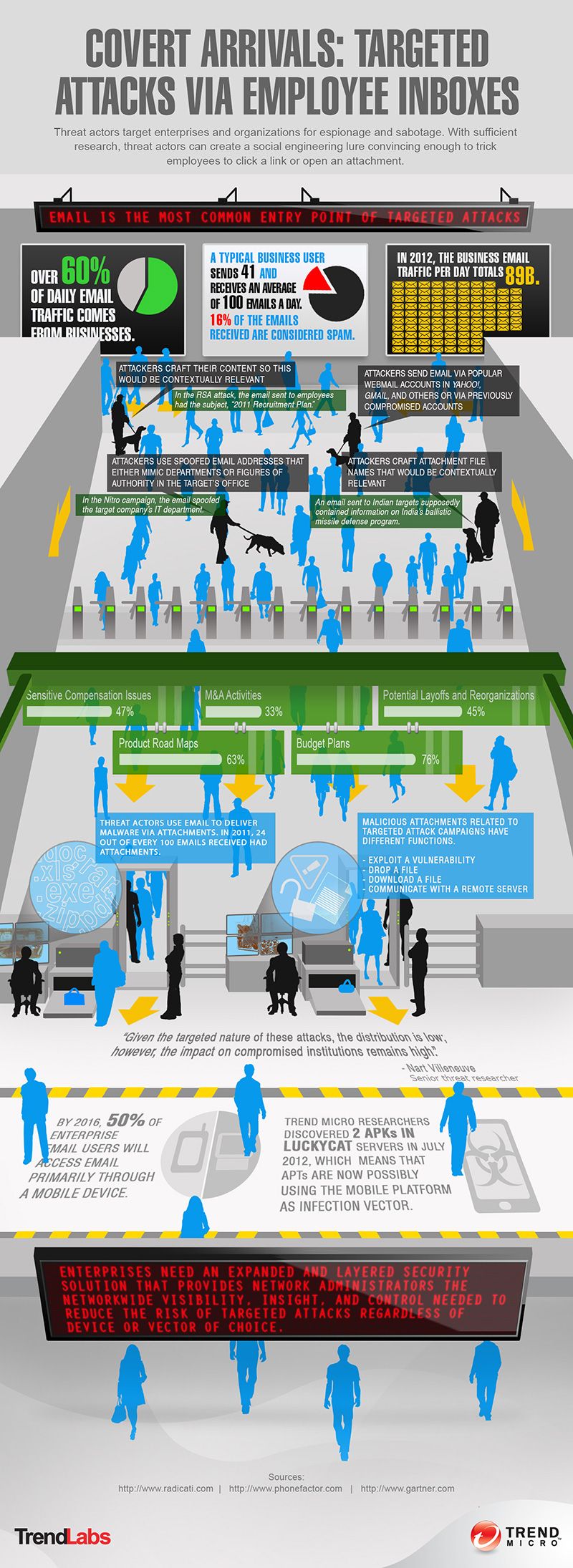
The Sophistication of the Hacking Scheme
This wasn't a simple password guess; this breach involved a highly sophisticated multi-pronged attack leveraging several techniques to bypass standard Office365 security measures. The attackers employed a combination of:
- Spear phishing: Highly targeted emails designed to mimic legitimate communications from trusted sources, fooling executives into revealing login credentials or clicking malicious links. These emails were personalized to each target, increasing their effectiveness.
- Credential stuffing: Using lists of stolen usernames and passwords obtained from previous data breaches to attempt logins on Office365 accounts. This technique is surprisingly effective if multi-factor authentication isn't in place.
- Exploitation of zero-day vulnerabilities: Taking advantage of previously unknown software flaws in either Office365 itself or in third-party applications integrated with it. This requires advanced technical skills and often involves the purchase of exploits on the dark web.
- Malware infections: Deploying malware to gain persistent access to compromised systems, allowing attackers to steal data, monitor activity, and maintain a foothold even after initial access is gained. This often involves social engineering techniques to trick users into downloading malicious attachments or clicking infected links.
The attackers likely employed advanced persistent threats (APTs), meaning they maintained a long-term presence within the targeted networks, allowing them to exfiltrate data over time without detection.
The Impact of the Breach on Businesses
The financial losses resulting from this type of breach are staggering. Affected businesses faced:
- Direct financial losses: Millions of dollars stolen directly from company accounts, along with the costs associated with incident response, forensic investigations, and legal fees.
- Reputational damage: Loss of customer trust, negative media coverage, and damage to the brand's image, leading to decreased sales and investor confidence.
- Legal and regulatory ramifications: Potential fines under regulations like GDPR (General Data Protection Regulation), costly lawsuits from affected individuals or clients, and potential regulatory scrutiny.
- Operational disruptions: Service interruptions, data leaks, intellectual property theft, and operational inefficiencies caused by the attack and the subsequent recovery efforts.
The long-term consequences of an Office365 security breach can severely impact a business's bottom line and long-term viability.
Identifying Vulnerabilities in Office365 Security
Many organizations unwittingly leave their Office365 environments vulnerable to attack. Common weaknesses include:
- Lack of multi-factor authentication (MFA): Relying solely on passwords leaves accounts highly susceptible to credential stuffing and phishing attacks. MFA adds an extra layer of security, significantly reducing the risk of unauthorized access.
- Weak password policies: Using easily guessable passwords or failing to enforce password complexity requirements creates vulnerabilities. Strong, unique passwords are crucial for effective Office365 security.
- Poorly configured email security settings: Failing to implement spam filters, anti-phishing measures, and secure email gateways leaves the organization open to various threats.
- Inadequate access controls: Granting excessive access privileges to employees can allow malicious insiders or attackers to move laterally within the network.
- Lack of regular security audits and penetration testing: Not proactively identifying and addressing vulnerabilities before they are exploited by attackers.
Best Practices for Protecting Executive Office365 Accounts
Strengthening your Executive Office365 account protection requires a multi-layered approach:
- Implement multi-factor authentication (MFA): This is the single most effective security measure to prevent unauthorized access.
- Enforce strong password policies: Require complex passwords, regular password changes, and password managers to enhance security.
- Enable advanced threat protection: Utilize Office365's built-in advanced threat protection features, including anti-phishing and anti-malware capabilities.
- Conduct regular security awareness training: Educate employees about phishing scams, safe browsing habits, and other security best practices.
- Utilize data loss prevention (DLP) tools: Prevent sensitive data from leaving the organization's network.
- Segment networks: Limit the impact of a breach by isolating critical systems and data.
- Regular Security Assessments and Penetration Testing: Proactively identify and mitigate vulnerabilities before they're exploited.
These measures, when implemented effectively, significantly reduce the risk of successful attacks and enhance overall Office365 security.
Conclusion: Safeguarding Your Executive Office365 Accounts from Future Breaches
The sophistication of the recent hacking scheme targeting executive Office365 accounts underscores the critical need for robust security measures. The financial and reputational risks associated with breaches are substantial. By implementing the best practices outlined above – from enforcing MFA and strong passwords to conducting regular security awareness training and penetration testing – organizations can significantly enhance their Executive Office365 account protection and safeguard against future attacks. Don't wait for a breach to happen; take proactive steps today to secure your organization's most valuable asset: its data and its executives' access to it. For further information on enhancing your Office365 security, consult resources from Microsoft and reputable cybersecurity firms.

Featured Posts
-
 Strengthening Nordic Security Synergies Between Swedens And Finlands Military Forces
Apr 22, 2025
Strengthening Nordic Security Synergies Between Swedens And Finlands Military Forces
Apr 22, 2025 -
 Massive Office365 Data Breach Executive Inboxes Targeted Millions Stolen
Apr 22, 2025
Massive Office365 Data Breach Executive Inboxes Targeted Millions Stolen
Apr 22, 2025 -
 New Ev Technology Partnership Saudi Aramco And Byd Collaborate
Apr 22, 2025
New Ev Technology Partnership Saudi Aramco And Byd Collaborate
Apr 22, 2025 -
 Russias Aerial Assault On Ukraine Us Peace Plan Amidst Deadly Barrage
Apr 22, 2025
Russias Aerial Assault On Ukraine Us Peace Plan Amidst Deadly Barrage
Apr 22, 2025 -
 Sweden And Finland Complementary Military Assets In A Pan Nordic Defense Strategy
Apr 22, 2025
Sweden And Finland Complementary Military Assets In A Pan Nordic Defense Strategy
Apr 22, 2025
Latest Posts
-
 Nba Sixth Man Of The Year Payton Pritchards Historic Season
May 12, 2025
Nba Sixth Man Of The Year Payton Pritchards Historic Season
May 12, 2025 -
 Pritchards Path To Nba Sixth Man Of The Year A Celtics Journey
May 12, 2025
Pritchards Path To Nba Sixth Man Of The Year A Celtics Journey
May 12, 2025 -
 Could Payton Pritchard Win Nba Sixth Man Of The Year A Celtics Chance
May 12, 2025
Could Payton Pritchard Win Nba Sixth Man Of The Year A Celtics Chance
May 12, 2025 -
 Celtics Payton Pritchard Wins Nba Sixth Man Of The Year
May 12, 2025
Celtics Payton Pritchard Wins Nba Sixth Man Of The Year
May 12, 2025 -
 Payton Pritchards Nba Sixth Man Of The Year Award Contention
May 12, 2025
Payton Pritchards Nba Sixth Man Of The Year Award Contention
May 12, 2025
