Federal Investigation: Millions Stolen Via Office365 Executive Inboxes
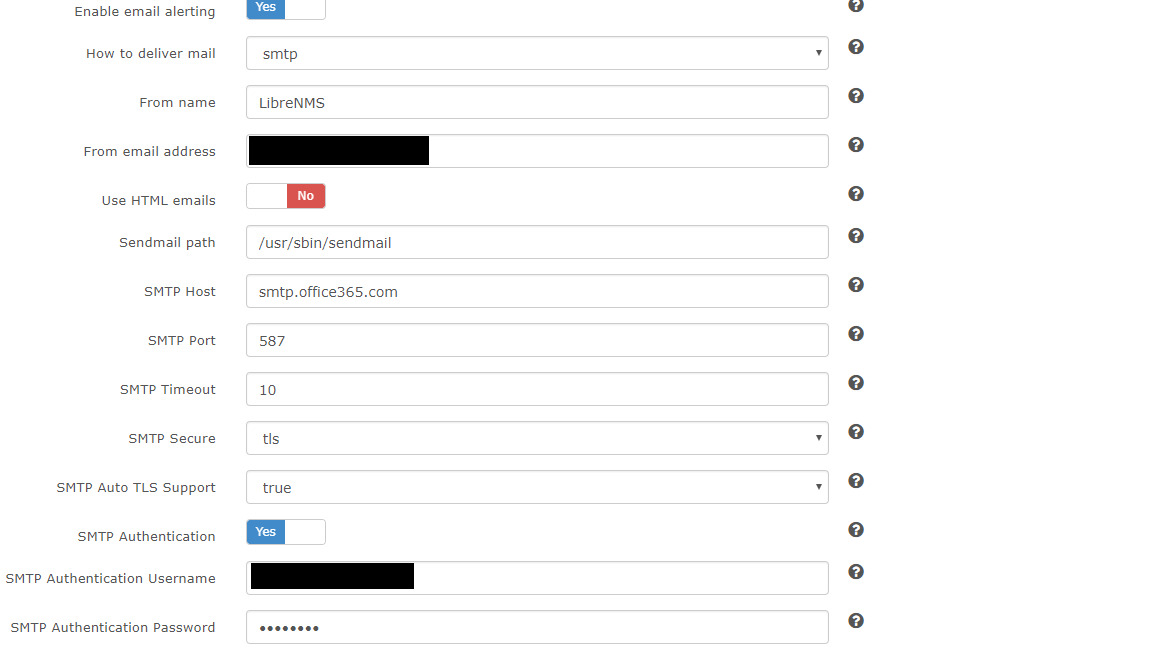
Table of Contents
The Modus Operandi: How the Office365 Executive Inbox Attacks Worked
These attacks leverage a combination of technical exploits and social engineering, often referred to as CEO fraud or Business Email Compromise (BEC). The perpetrators meticulously craft their attacks to exploit trust relationships within an organization, targeting high-level executives who often have access to sensitive financial information and authorization to initiate large transactions.
- Spear phishing emails mimicking legitimate communications: Attackers create highly convincing emails that appear to originate from trusted sources, such as a colleague, a client, or even a board member. These emails often contain urgent requests for immediate action, such as wire transfers or payment approvals.
- Use of social engineering tactics to gain trust and bypass security protocols: Beyond realistic email design, attackers employ psychological manipulation to pressure victims into acting quickly without verification. Creating a sense of urgency or leveraging a known relationship is key to their success.
- Exploitation of vulnerabilities in Office365 account settings: While MFA is a crucial layer of security, attackers may exploit weaknesses in other account settings, potentially gaining access through compromised passwords or exploiting vulnerabilities in third-party applications integrated with Office365.
- Rapid wire transfers once access is gained: Once access is gained, attackers swiftly initiate wire transfers to pre-arranged accounts, often before the compromised account is flagged.
- Use of mules and offshore accounts to launder stolen funds: The stolen funds are quickly moved through a network of mules and offshore accounts to obscure the trail and make recovery difficult.
The Scale of the Problem: Financial Losses and Affected Businesses
The financial impact of these Office365 executive inbox attacks is staggering. The investigation revealed millions of dollars lost across numerous businesses of varying sizes. While specific numbers from this particular investigation may be confidential due to ongoing legal proceedings, similar attacks have resulted in significant losses for both large corporations and small businesses alike.
- Statistics on the average loss per incident: Reports from cybersecurity firms suggest average losses per incident can range from tens of thousands to millions of dollars.
- Number of businesses impacted by this specific investigation (if available): Due to the sensitive nature of ongoing investigations, precise figures are often not publicly released.
- Industries most frequently targeted: Industries handling large sums of money, such as finance, real estate, and construction, are prime targets for these attacks. However, no industry is immune.
Strengthening Your Defenses: Protecting Your Office365 Executive Inboxes
Protecting against these sophisticated attacks requires a multi-layered approach to security that combines technical safeguards with employee training and awareness. A layered security approach is vital because no single solution provides complete protection.
- Implementing robust multi-factor authentication (MFA) beyond basic security questions: Use a strong MFA system that goes beyond simple security questions, incorporating methods such as authenticator apps, hardware tokens, or biometrics.
- Employee security awareness training to recognize phishing attempts: Regular training sessions are crucial to educate employees on identifying phishing emails and reporting suspicious activity. Simulations and practical examples are highly effective.
- Regular security audits and penetration testing of Office365 systems: Proactive security audits and penetration testing can help identify vulnerabilities before attackers exploit them.
- Implementing email authentication protocols like SPF, DKIM, and DMARC: These protocols help verify the authenticity of emails, reducing the risk of spoofing.
- Use of advanced threat protection tools within Office365: Office365 offers various advanced threat protection features, including anti-phishing and anti-malware capabilities. Leverage these tools to their fullest extent.
- Establish strict financial controls and multiple approvals for large transfers: Implementing a system of checks and balances for financial transactions, requiring multiple approvals for large sums of money, can significantly reduce the risk of fraudulent transfers.
- Regularly review user permissions and access controls: Ensure that only authorized individuals have access to sensitive financial information and the authority to make financial transactions.
The Role of Human Error in Office365 Breaches
Human error remains a significant contributing factor to successful attacks. Even with robust security measures in place, a single click on a malicious link or a failure to report a suspicious email can compromise the entire system.
- Examples of common human errors that lead to breaches: Clicking on malicious links in emails, downloading attachments from unknown senders, reusing passwords, and ignoring security warnings.
- Best practices for training employees to identify and report suspicious emails: Provide regular, interactive training sessions, including phishing simulations, to equip employees with the skills to identify and report suspicious emails promptly.
Conclusion
The federal investigation into millions stolen via compromised Office365 executive inboxes serves as a stark reminder of the ever-evolving threats facing businesses. The attackers' sophisticated methods and the significant financial losses highlight the critical need for proactive and layered security measures. Protecting your organization from Office365 executive inbox attacks requires a commitment to robust security protocols, comprehensive employee training, and constant vigilance against phishing attempts. These attacks are not just a technical issue; they are a human issue as well. Addressing both technical and human factors is key to effective protection.
Call to Action: Don't become another victim. Protect your organization from Office365 executive inbox attacks by implementing robust security protocols, providing comprehensive employee training, and staying vigilant against phishing attempts. Take action today to safeguard your business from similar attacks and secure your financial future. Learn more about strengthening your Office365 security now!

Featured Posts
-
 Ai Competition The Us And Chinas Dominance Pushes Mideast Players Aside
May 07, 2025
Ai Competition The Us And Chinas Dominance Pushes Mideast Players Aside
May 07, 2025 -
 Donovan Mitchells Popcorn Prank A Cavs Rookies Initiation
May 07, 2025
Donovan Mitchells Popcorn Prank A Cavs Rookies Initiation
May 07, 2025 -
 Understanding Front Loading A Strategy For Malaysian Ringgit Myr Exchange Rate Stability In Exports
May 07, 2025
Understanding Front Loading A Strategy For Malaysian Ringgit Myr Exchange Rate Stability In Exports
May 07, 2025 -
 Who Wants To Be A Millionaire Celebrity Special A Guide For Aspiring Contestants
May 07, 2025
Who Wants To Be A Millionaire Celebrity Special A Guide For Aspiring Contestants
May 07, 2025 -
 Lotto 6aus49 Die Gewinnzahlen Des 12 April 2025
May 07, 2025
Lotto 6aus49 Die Gewinnzahlen Des 12 April 2025
May 07, 2025
Latest Posts
-
 Alkhtwt Almlkyt Almghrbyt Tkhtt Lzyadt Edd Rhlatha Byn Albrazyl Walmghrb
May 07, 2025
Alkhtwt Almlkyt Almghrbyt Tkhtt Lzyadt Edd Rhlatha Byn Albrazyl Walmghrb
May 07, 2025 -
 Zyadt Rhlat Alkhtwt Almlkyt Almghrbyt Almbashrt Byn Saw Bawlw Waldar Albydae
May 07, 2025
Zyadt Rhlat Alkhtwt Almlkyt Almghrbyt Almbashrt Byn Saw Bawlw Waldar Albydae
May 07, 2025 -
 Tyrt Rhlat Alkhtwt Almlkyt Almghrbyt Byn Saw Bawlw Waldar Albydae Strtfe
May 07, 2025
Tyrt Rhlat Alkhtwt Almlkyt Almghrbyt Byn Saw Bawlw Waldar Albydae Strtfe
May 07, 2025 -
 Alkhtwt Almlkyt Almghrbyt Tezz Rhlatha Byn Saw Bawlw Waldar Albydae
May 07, 2025
Alkhtwt Almlkyt Almghrbyt Tezz Rhlatha Byn Saw Bawlw Waldar Albydae
May 07, 2025 -
 Alkhtwt Almlkyt Almghrbyt Zyadt Rhlat Saw Bawlw Aldar Albydae
May 07, 2025
Alkhtwt Almlkyt Almghrbyt Zyadt Rhlat Saw Bawlw Aldar Albydae
May 07, 2025
