Hacker Makes Millions Targeting Executive Office365 Accounts

Table of Contents
The Hacker's Methods: Sophisticated Phishing and Exploits
The methods employed by hackers targeting executive Office365 accounts are increasingly sophisticated, often combining several techniques to maximize their chances of success. These attacks rely heavily on social engineering and exploiting known vulnerabilities within the Office365 ecosystem. Key methods include:
- Spear Phishing: These highly targeted phishing scams use personalized emails mimicking legitimate communications from known contacts or organizations. They often contain malicious links or attachments designed to deliver malware.
- Credential Stuffing: Hackers use lists of stolen usernames and passwords obtained from other breaches to attempt to access Office365 accounts. This is particularly effective if weak or reused passwords are used.
- Exploiting Vulnerabilities: Hackers actively seek out and exploit known vulnerabilities in Office365 applications or its underlying infrastructure. Keeping software updated and patched is crucial to mitigate this risk.
- Malware Delivery: Once access is gained, hackers deploy malware to steal login credentials, sensitive data, and further compromise the network. This can include ransomware, which encrypts data and demands a ransom for its release.
- Multi-Factor Authentication (MFA) Bypass: While MFA provides significant protection, hackers may attempt to bypass it through social engineering techniques, such as manipulating employees into revealing their authentication codes.
The High Value of Executive Office365 Accounts
Executive Office365 accounts represent a highly lucrative target for cybercriminals due to the privileged access they provide. These accounts often control:
- Financial Data: Access to sensitive financial records, transaction details, and bank account information allows hackers to initiate fraudulent transactions or steal funds.
- Strategic Plans & Intellectual Property: Executive accounts frequently contain confidential strategic plans, intellectual property, and sensitive business information that can be sold to competitors or used for blackmail.
- Confidential Communications: Access to email communications allows hackers to gather intelligence, identify vulnerabilities, and potentially compromise other accounts or systems.
- Internal Network Access: Executive accounts often grant broad access to the internal network, potentially allowing hackers to move laterally and compromise other valuable data sources. This presents a significant insider threat risk.
The Financial Impact and Long-Term Consequences
The financial consequences of an Office365 executive account breach can be devastating. Beyond the direct financial losses from data theft or ransom demands, businesses face:
- Data Recovery Costs: Recovering compromised data and restoring systems can be an expensive and time-consuming process, requiring specialized expertise and resources.
- Legal and Regulatory Fines: Data breaches can trigger significant legal fees and regulatory fines, especially if sensitive personal data (PII) is compromised. Compliance violations can lead to further penalties.
- Reputational Damage: A data breach can severely damage a company's reputation, impacting customer trust and potentially leading to lost business. This reputational damage can be long-lasting and difficult to repair.
- Business Disruption: The disruption to business operations caused by a data breach can be substantial, impacting productivity and revenue streams. This disruption can have significant long-term financial consequences.
Protecting Your Executive Office365 Accounts: Best Practices
Protecting your organization from these devastating attacks requires a multi-layered approach to Office365 security. Key strategies include:
- Strong Password Policies: Enforce the use of complex, unique passwords and regularly update them. Implement password management tools to facilitate this.
- Multi-Factor Authentication (MFA): Mandate MFA for all executive accounts and ideally, for all users. This adds an extra layer of security, significantly reducing the risk of unauthorized access.
- Security Awareness Training: Regularly train employees on recognizing and avoiding phishing scams and other social engineering tactics. This is crucial in preventing users from falling victim to malicious attacks.
- Regular Security Audits: Conduct periodic security audits to identify vulnerabilities in your Office365 environment and implement necessary remediation measures.
- Incident Response Plan: Develop and regularly test a comprehensive incident response plan to effectively manage and mitigate the impact of a security breach. This plan should include clear communication protocols, data recovery strategies, and forensic investigation procedures.
- Threat Intelligence: Utilize threat intelligence feeds to proactively identify and mitigate emerging threats. This proactive approach enables timely responses to potential vulnerabilities.
Conclusion
The successful targeting of executive Office365 accounts by hackers underscores the growing sophistication and financial motivation behind cybercrime. The financial and reputational consequences of such breaches are significant, demanding a robust and proactive approach to Office365 security. By implementing strong password policies, enabling multi-factor authentication, investing in comprehensive security awareness training, and developing a robust incident response plan, businesses can significantly reduce their risk and protect their valuable assets. Don't become the next victim. Learn more about protecting your Office365 executive accounts and implement a comprehensive security strategy today. Contact a cybersecurity professional for assistance in securing your organization.

Featured Posts
-
 Will Trumps Promise Of Factory Job Returns Become Reality
May 21, 2025
Will Trumps Promise Of Factory Job Returns Become Reality
May 21, 2025 -
 Analyzing The 2025 Decline Of D Wave Quantum Inc Qbts Stock
May 21, 2025
Analyzing The 2025 Decline Of D Wave Quantum Inc Qbts Stock
May 21, 2025 -
 Switzerland Rebukes Chinas Military Exercises
May 21, 2025
Switzerland Rebukes Chinas Military Exercises
May 21, 2025 -
 Transferz Krijgt Financiering Van Abn Amro Nieuwe Mogelijkheden Voor Digitale Transacties
May 21, 2025
Transferz Krijgt Financiering Van Abn Amro Nieuwe Mogelijkheden Voor Digitale Transacties
May 21, 2025 -
 Experience Hellfest Au Noumatrouff De Mulhouse
May 21, 2025
Experience Hellfest Au Noumatrouff De Mulhouse
May 21, 2025
Latest Posts
-
 Reddits Ai Stock Picks 12 Companies To Consider
May 21, 2025
Reddits Ai Stock Picks 12 Companies To Consider
May 21, 2025 -
 Weather Alert High Winds And Severe Storms Approaching Your Area
May 21, 2025
Weather Alert High Winds And Severe Storms Approaching Your Area
May 21, 2025 -
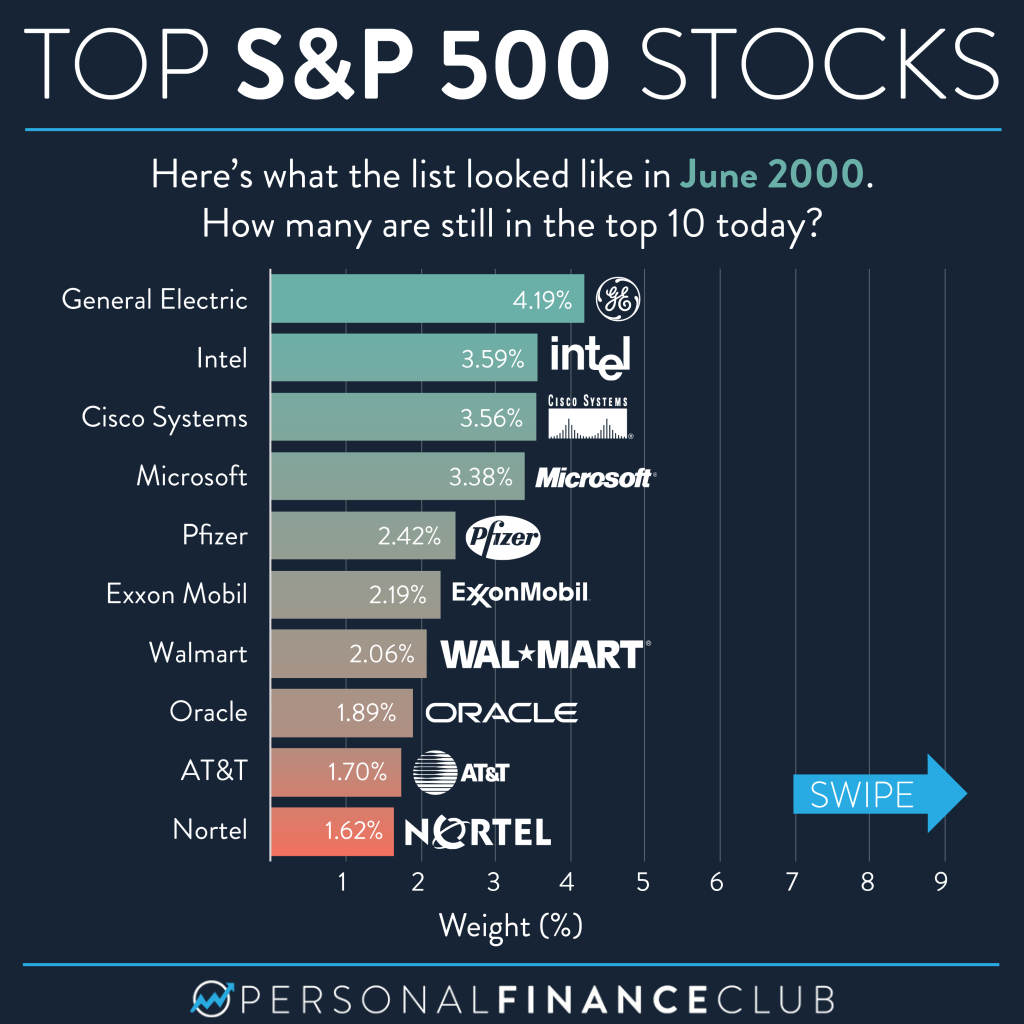 12 Popular Ai Stocks From Reddit A Detailed Overview
May 21, 2025
12 Popular Ai Stocks From Reddit A Detailed Overview
May 21, 2025 -
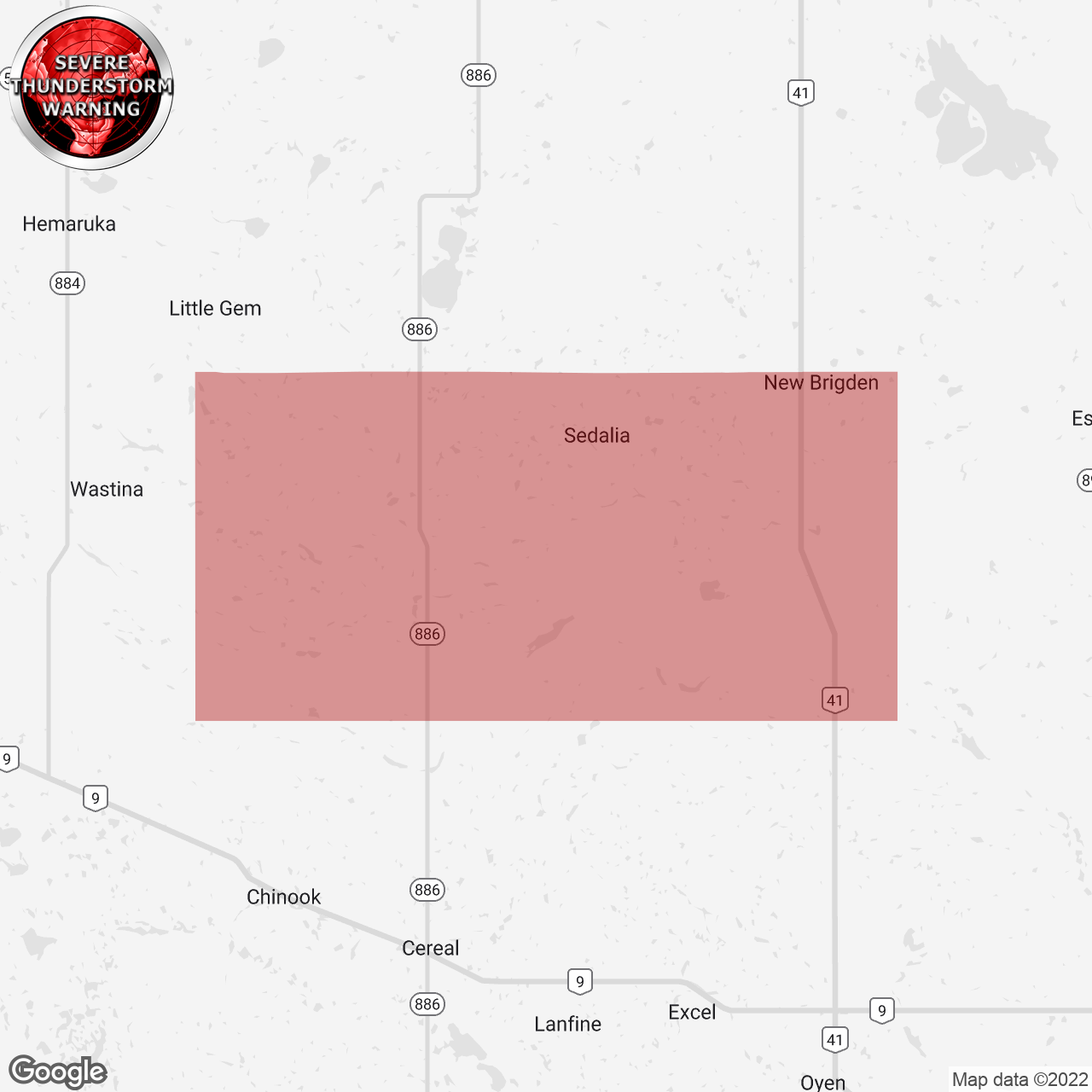 Strong Wind And Severe Storm Warning Take Action Now
May 21, 2025
Strong Wind And Severe Storm Warning Take Action Now
May 21, 2025 -
 Confirmed Collins Aerospace Implements Layoffs In Cedar Rapids
May 21, 2025
Confirmed Collins Aerospace Implements Layoffs In Cedar Rapids
May 21, 2025
