Massive Office365 Breach: Executive Inboxes Targeted, Millions Stolen
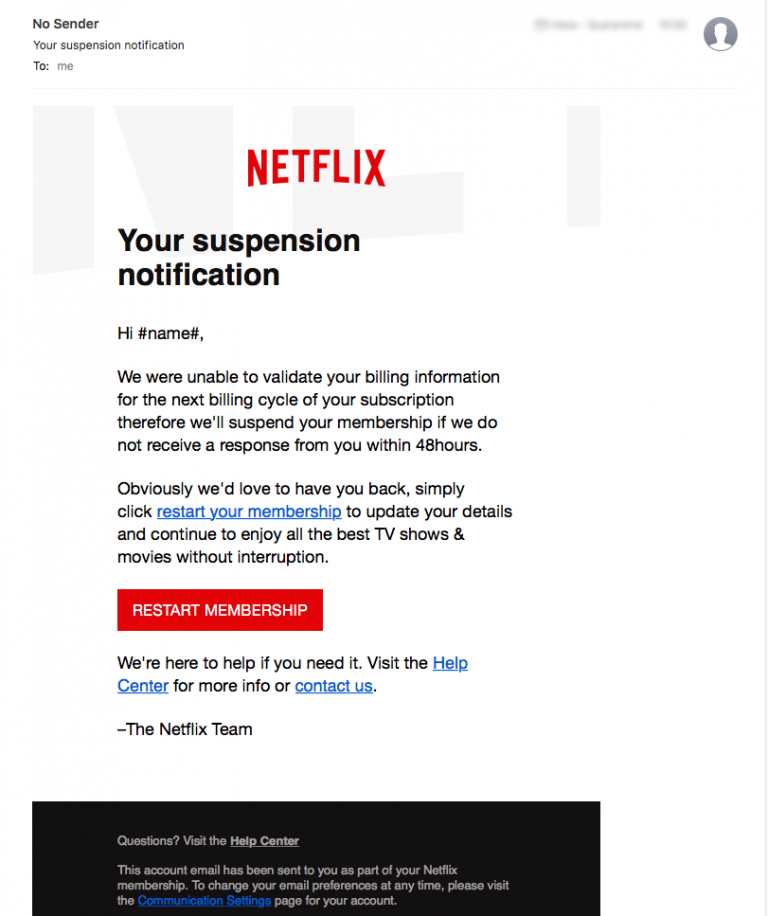
Table of Contents
The Scope of the Office365 Breach: A Deep Dive into the Numbers
This Office365 breach wasn't a minor incident; it was a significant data breach with far-reaching consequences. The sheer scale of the attack underscores the critical need for robust cybersecurity measures.
Financial Losses: Quantify the millions stolen, citing sources if available. Use keywords like "financial impact," "data theft," and "ransomware attack" (if applicable).
The financial impact of this Office365 breach is staggering. While precise figures are often withheld for legal and security reasons, reports suggest losses in the millions of dollars for several affected organizations. These losses stem from various sources:
- Lost revenue: Disruption to operations due to compromised systems and data loss directly impacts revenue streams.
- Legal fees: Responding to the breach, investigating the incident, and managing potential litigation significantly increases legal costs.
- Recovery costs: Restoring systems, recovering data, and implementing enhanced security measures all incur significant expenses.
- Reputational damage: The loss of trust from clients and partners can lead to long-term financial repercussions. Some companies have even had to file insurance claims to cover a portion of these substantial losses.
Data Compromised: Detail the types of sensitive data stolen (e.g., financial records, intellectual property, customer data, personal information). Keywords: "sensitive data," "PII breach," "intellectual property theft," "customer data breach."
The stolen data represents a significant PII breach and a serious cybersecurity threat. The attackers gained access to a treasure trove of sensitive information, including:
- Financial records: Bank account details, transaction histories, and financial projections were compromised, leading to potential fraud and identity theft.
- Intellectual property: Confidential business plans, trade secrets, and research data were stolen, potentially giving competitors a significant advantage.
- Customer data: Personally identifiable information (PII) of customers, including names, addresses, email addresses, and phone numbers, was exposed, increasing the risk of identity theft and reputational damage.
- Internal communications: Emails and other internal communications revealed sensitive strategies and decision-making processes, undermining operational security.
Number of Victims: Specify the number of organizations and individuals affected by the breach. Use keywords like "victim count," "compromised accounts," and "attack surface."
While the exact victim count remains undisclosed for many organizations, reports indicate that hundreds of organizations and potentially millions of individuals were affected by this wide-ranging Office365 breach. The attack surface was substantial, impacting both large corporations and smaller businesses across various industries.
- The wide geographical spread of victims highlights the global reach of this sophisticated cyberattack.
- The vulnerability of seemingly secure systems was clearly demonstrated by the broad range of organizations impacted, highlighting the need for comprehensive cybersecurity.
How the Office365 Breach Occurred: Unraveling the Attack Vectors
Understanding how this Office365 breach occurred is crucial for developing effective preventative measures. The attack leveraged a combination of sophisticated techniques.
Phishing and Social Engineering: Detail how the attackers gained initial access. Keywords: "phishing attacks," "social engineering," "spear phishing," "credential stuffing."
The initial access point for many of the breaches was sophisticated spear phishing campaigns. Attackers used highly targeted emails that appeared to be legitimate communications from trusted sources. These emails often contained malicious links or attachments designed to:
- Install malware on victim machines.
- Trick users into revealing their Office365 credentials.
- Gain access to the network through compromised accounts. Credential stuffing, using previously stolen login credentials, was also likely employed to access accounts.
Exploiting Vulnerabilities: Discuss any known vulnerabilities in Office365 exploited by the attackers. Keywords: "zero-day exploits," "software vulnerabilities," "patch management," "security updates."
While specific vulnerabilities haven't been publicly disclosed in all cases, it's highly likely that attackers exploited known vulnerabilities in Office365 or its associated applications. This highlights the importance of:
- Regularly applying security updates and patches.
- Maintaining up-to-date software.
- Proactive vulnerability assessment and penetration testing to identify and mitigate potential weaknesses.
Insider Threats (if applicable): Discuss the possibility of insider involvement. Keywords: "insider threat," "malicious insiders," "data leakage."
While not confirmed in all cases, the possibility of insider threats cannot be entirely ruled out. Malicious insiders with access to privileged accounts could facilitate the breach and increase the scale of data leakage. Thorough investigation is needed to determine the full extent of involvement, if any.
Protecting Your Organization from a Similar Office365 Breach: Proactive Security Measures
The best defense against an Office365 breach is a proactive and multi-layered security strategy.
Multi-Factor Authentication (MFA): Emphasize the importance of MFA. Keywords: "multi-factor authentication," "two-factor authentication," "password management," "identity and access management (IAM)."
Implementing multi-factor authentication (MFA) is paramount. MFA adds an extra layer of security by requiring more than just a password to access accounts. This significantly reduces the risk of unauthorized access even if credentials are compromised.
- MFA significantly enhances security by requiring a second verification factor, such as a code from a mobile app or a security key.
- Strong password management policies are crucial and should be paired with MFA for optimal protection.
Regular Security Audits and Penetration Testing: Highlight the need for proactive security measures. Keywords: "security audit," "penetration testing," "vulnerability assessment," "red teaming."
Regular security audits and penetration testing are essential for identifying and mitigating vulnerabilities before attackers can exploit them. These proactive measures help strengthen your organization's overall security posture.
- Vulnerability assessments scan systems for known weaknesses.
- Penetration testing simulates real-world attacks to identify exploitable vulnerabilities.
- Red teaming exercises involve simulating advanced persistent threats.
Employee Security Awareness Training: Stress the crucial role of employee education. Keywords: "security awareness training," "phishing simulations," "cybersecurity training," "social engineering awareness."
Employee education is a critical component of cybersecurity. Regular security awareness training empowers employees to identify and avoid phishing attacks and other social engineering tactics.
- Conduct regular phishing simulations to test employee awareness and identify training gaps.
- Provide cybersecurity training that covers various threats and best practices.
Robust Data Backup and Recovery Plans: Explain the importance of having a reliable backup and recovery strategy. Keywords: "data backup," "data recovery," "disaster recovery," "business continuity."
A robust data backup and recovery plan is essential for minimizing the impact of a breach. Regular backups ensure that you can restore your data quickly and efficiently in the event of a security incident.
- Cloud-based backup solutions provide a secure and offsite backup.
- Regular testing of your backup and recovery plan is crucial to ensure its effectiveness.
Conclusion: Preventing Future Office365 Breaches: A Call to Action
This massive Office365 breach underscores the critical need for robust cybersecurity measures. The scale of the financial losses and the sensitive data compromised highlight the devastating consequences of inadequate security. By implementing multi-factor authentication, conducting regular security audits and penetration testing, investing in employee security awareness training, and establishing a robust data backup and recovery plan, organizations can significantly reduce their risk of experiencing a similar Office365 data breach. Don't wait for a catastrophic event—take proactive steps today to secure your Office365 environment and prevent future cybersecurity threats. Consult with cybersecurity experts to assess your current security posture and develop a comprehensive plan to protect your organization.

Featured Posts
-
 Psg Invests In Global Innovation With New Doha Labs
May 08, 2025
Psg Invests In Global Innovation With New Doha Labs
May 08, 2025 -
 The Aftermath Of La Fires Examining Allegations Of Landlord Price Gouging
May 08, 2025
The Aftermath Of La Fires Examining Allegations Of Landlord Price Gouging
May 08, 2025 -
 Sufian Commends Gcci President For Successful Expo 2025 Organization
May 08, 2025
Sufian Commends Gcci President For Successful Expo 2025 Organization
May 08, 2025 -
 Oklahoma Citys Tough Road Trip Continues Matchup Against Memphis
May 08, 2025
Oklahoma Citys Tough Road Trip Continues Matchup Against Memphis
May 08, 2025 -
 Lotto Draw Results Check The Latest Numbers For Lotto Plus 1 And 2
May 08, 2025
Lotto Draw Results Check The Latest Numbers For Lotto Plus 1 And 2
May 08, 2025
