Millions Stolen: Insider Reveals Exec Office365 Account Compromise

Table of Contents
H2: The Insider's Account: How the Breach Occurred
Our source, a former senior IT specialist at a large multinational corporation (who wishes to remain anonymous for confidentiality reasons), revealed a disturbingly common scenario. This individual had access to sensitive organizational data and, unfortunately, witnessed firsthand how a seemingly minor oversight led to a major Office365 account compromise.
The breach started with a sophisticated phishing campaign targeting executive accounts. The attackers used highly realistic emails mimicking legitimate internal communications, designed to bypass initial email filters. The malicious emails contained links to websites mirroring the company's intranet, where unsuspecting executives unknowingly entered their credentials. This was compounded by a lack of robust security protocols.
- Specific vulnerabilities exploited: Weak password policies, absence of multi-factor authentication (MFA).
- Step-by-step breakdown of the attack process: Phishing email -> compromised credentials -> access to executive Office365 accounts -> data exfiltration.
- Lack of multi-factor authentication (MFA): This single factor proved catastrophic, allowing attackers easy access even after obtaining credentials.
- Inadequate employee security training: A lack of awareness regarding phishing tactics left executives vulnerable to these attacks.
H2: The Financial and Reputational Damage
The consequences were devastating. Millions were stolen through fraudulent wire transfers initiated from compromised accounts. The attackers also accessed and exfiltrated sensitive financial data, intellectual property, and confidential client information. The repercussions extended far beyond the immediate financial loss.
- Loss of sensitive financial data: This led to significant financial losses and potential legal battles.
- Intellectual property theft: The theft of trade secrets caused irreparable damage to the company's competitive advantage.
- Damage to customer trust: News of the breach severely eroded customer confidence, impacting future business.
- Stock price decline: The company experienced a significant drop in its stock value following the public disclosure of the incident.
H2: Lessons Learned and Best Practices for Enhanced Office365 Security
The insider's account highlights critical weaknesses in cybersecurity practices. Preventing similar Office365 account compromises requires a multi-layered approach focusing on proactive security measures and employee education.
- Implementing strong password policies: Enforce complex passwords with mandatory character types and regular changes.
- Utilizing multi-factor authentication (MFA) for all accounts: This adds an extra layer of security, significantly reducing the risk of unauthorized access.
- Regular security awareness training for employees: Educate employees about phishing scams, malware, and other social engineering tactics.
- Employing advanced threat protection solutions: Invest in advanced security solutions that can detect and prevent sophisticated attacks.
- Conducting regular security audits: Regular assessments identify vulnerabilities and ensure security protocols are effective.
3. Conclusion: Protecting Your Executive Office365 Accounts from Compromise
This insider's account serves as a stark reminder of the devastating consequences of neglecting cybersecurity. An Office365 account compromise can inflict crippling financial losses, irreversible reputational damage, and severe legal repercussions. Protecting your executive accounts and your organization's future demands a robust, proactive approach. Don't become the next victim of an Office365 account compromise. Take action today to protect your executive accounts and secure your organization's future by implementing the best practices outlined above. For further assistance, explore resources on multi-factor authentication (MFA) setup and comprehensive cybersecurity best practices guides available online. Invest in your security – it's an investment in your future.

Featured Posts
-
 From Scatological Documents To Engaging Podcast The Power Of Ai
May 05, 2025
From Scatological Documents To Engaging Podcast The Power Of Ai
May 05, 2025 -
 Ftc Launches Probe Into Open Ais Chat Gpt A Deep Dive
May 05, 2025
Ftc Launches Probe Into Open Ais Chat Gpt A Deep Dive
May 05, 2025 -
 Blake Lively And Anna Kendrick Reunite Amidst Feud Rumors At Premiere
May 05, 2025
Blake Lively And Anna Kendrick Reunite Amidst Feud Rumors At Premiere
May 05, 2025 -
 The Accountant 2 And The Essential Role Of Anna Kendrick In A Potential Third Film
May 05, 2025
The Accountant 2 And The Essential Role Of Anna Kendrick In A Potential Third Film
May 05, 2025 -
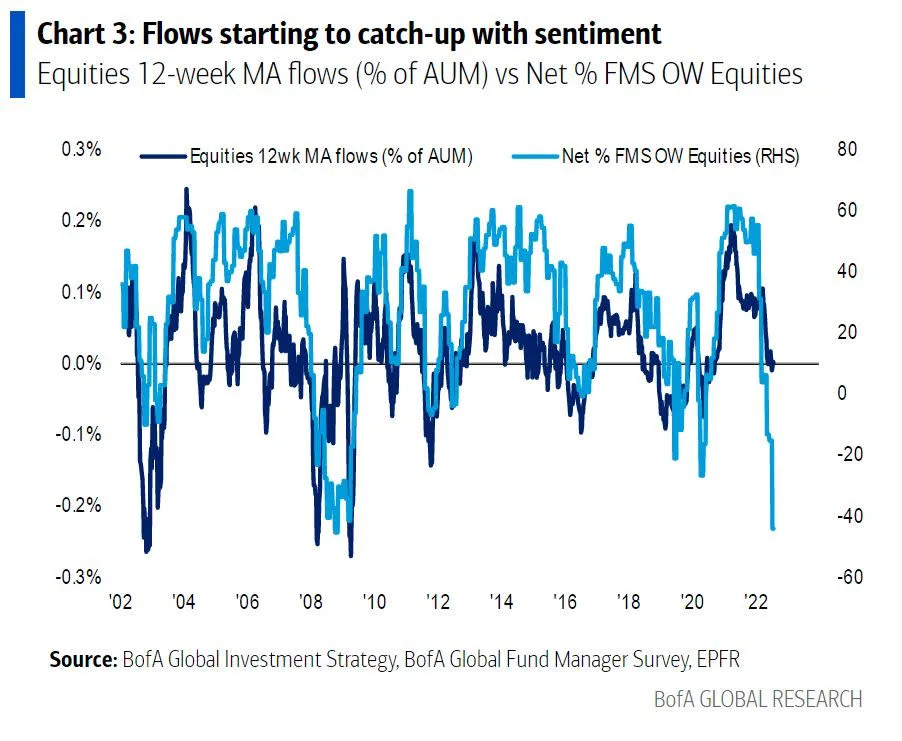 Should Investors Worry About Current Stock Market Valuations Bof As View
May 05, 2025
Should Investors Worry About Current Stock Market Valuations Bof As View
May 05, 2025
Latest Posts
-
 Paddy The Baddy Pimblett Hosts Lavish Yacht Party After Ufc 314 Win
May 05, 2025
Paddy The Baddy Pimblett Hosts Lavish Yacht Party After Ufc 314 Win
May 05, 2025 -
 Ufc 314 Paddy Pimbletts Exclusive Yacht Party Following Dominant Win
May 05, 2025
Ufc 314 Paddy Pimbletts Exclusive Yacht Party Following Dominant Win
May 05, 2025 -
 Paddy Pimbletts Post Fight Yacht Party Ufc 314 Celebration
May 05, 2025
Paddy Pimbletts Post Fight Yacht Party Ufc 314 Celebration
May 05, 2025 -
 Ufc 314 Volkanovski Lopes Headliner And Full Fight Card Preview
May 05, 2025
Ufc 314 Volkanovski Lopes Headliner And Full Fight Card Preview
May 05, 2025 -
 Alexander Volkanovski Vs Diego Lopes Ufc 314 Fight Card Analysis
May 05, 2025
Alexander Volkanovski Vs Diego Lopes Ufc 314 Fight Card Analysis
May 05, 2025
