Office 365 Breach: Execs Targeted In Millions-Dollar Scheme

Table of Contents
The Sophistication of the Office 365 Breach
This particular Office 365 breach showcased the advanced tactics employed by modern cybercriminals. Targeting executives is a strategic move; their accounts often grant access to sensitive company data and critical systems, maximizing the potential payoff. The attackers used a multi-pronged approach, combining several techniques for maximum effectiveness:
- Spear-phishing: Highly personalized emails mimicking legitimate communications from trusted sources were sent to executives, cleverly designed to bypass standard email filters. These often contained malicious links or attachments leading to malware downloads.
- Exploitation of known vulnerabilities: The attackers exploited known vulnerabilities in Office 365, leveraging zero-day exploits or known unpatched software to gain unauthorized access. Regular updates and patching are vital to mitigating this risk.
- Credential stuffing: Stolen credentials obtained from previous breaches were used to attempt access to Office 365 accounts. This highlights the importance of strong password policies and multi-factor authentication.
- Lateral movement: Once inside the network, attackers used stolen credentials to move laterally, gaining access to more sensitive data and systems. Robust access control is critical to limiting the damage from a successful breach.
- Data exfiltration: Sophisticated techniques were used to exfiltrate stolen data, often using encrypted channels to avoid detection. This data included highly sensitive information, demonstrating the potential for significant long-term damage.
Financial Impact and Data Breaches
The financial impact of this Office 365 breach was staggering, resulting in millions of dollars in losses. Beyond the immediate financial losses, the long-term consequences are far-reaching:
- Reputational damage: The breach severely damaged the company’s reputation, impacting investor confidence and customer loyalty.
- Legal liabilities: The company faced significant legal liabilities due to the exposure of sensitive customer data and potential violations of data privacy regulations like GDPR and CCPA.
The types of data compromised were extensive, including:
- Financial transactions and banking details: This allowed attackers to commit further financial crimes.
- Proprietary business information: Trade secrets and intellectual property were exposed, giving competitors a significant advantage.
- Customer data and personal identifiable information (PII): This put customers at risk of identity theft and fraud.
- Strategic plans and future projects: This compromised the company’s future plans and competitive advantage.
Preventing Office 365 Breaches: Security Best Practices
Protecting your organization from similar Office 365 breaches requires a multi-layered approach focusing on proactive security measures:
- Multi-factor authentication (MFA): Implementing MFA for all accounts significantly reduces the risk of unauthorized access, even if credentials are compromised.
- Regular security awareness training: Educating employees about phishing scams and other social engineering tactics is crucial. Simulations and regular training are essential.
- Robust access control measures: Implementing the principle of least privilege limits the damage caused by compromised accounts.
- Patching and updating: Regularly updating Office 365 and all related software is crucial to closing security vulnerabilities.
- Advanced threat protection: Employing advanced threat protection solutions can help detect and prevent malicious activity before it causes significant damage.
- Strong password policies: Enforcing strong, unique passwords and using a password manager minimizes the risk of credential stuffing.
- Email security solutions: Implement robust email security solutions including spam filters, anti-malware, and email authentication protocols like SPF, DKIM, and DMARC.
- Regular monitoring: Continuously monitor user activity and access logs for suspicious behavior.
The Role of Cybersecurity Insurance in Mitigating Office 365 Breach Risks
Cybersecurity insurance plays a vital role in mitigating the financial burden associated with Office 365 breaches. A comprehensive policy can cover a wide range of expenses:
- Incident response costs: Covering the cost of expert consultants to investigate and remediate the breach.
- Legal and regulatory fines: Assisting with legal fees and regulatory penalties resulting from data breaches.
- Public relations assistance: Helping manage the reputational damage and communicating effectively with stakeholders.
- Data recovery and restoration costs: Covering the expenses of recovering and restoring compromised data.
Conclusion: Protecting Your Organization from Office 365 Breaches
The case study highlights the severe consequences of targeted Office 365 breaches, emphasizing the critical need for robust security measures. The financial losses, reputational damage, and legal liabilities associated with such breaches can be devastating. Don't become the next victim of an Office 365 breach. Implement the preventative measures discussed in this article – including multi-factor authentication, regular security awareness training, robust access control, and advanced threat protection – to safeguard your organization's sensitive data and financial stability. Prioritizing Office 365 security is not just a best practice; it's a business imperative. Invest in your security today; your organization's future depends on it.

Featured Posts
-
 Lara Crofts Fortnite Comeback Leak Reveals Release Date Hints
May 03, 2025
Lara Crofts Fortnite Comeback Leak Reveals Release Date Hints
May 03, 2025 -
 Play Station Network Christmas Voucher Glitch Compensation Details
May 03, 2025
Play Station Network Christmas Voucher Glitch Compensation Details
May 03, 2025 -
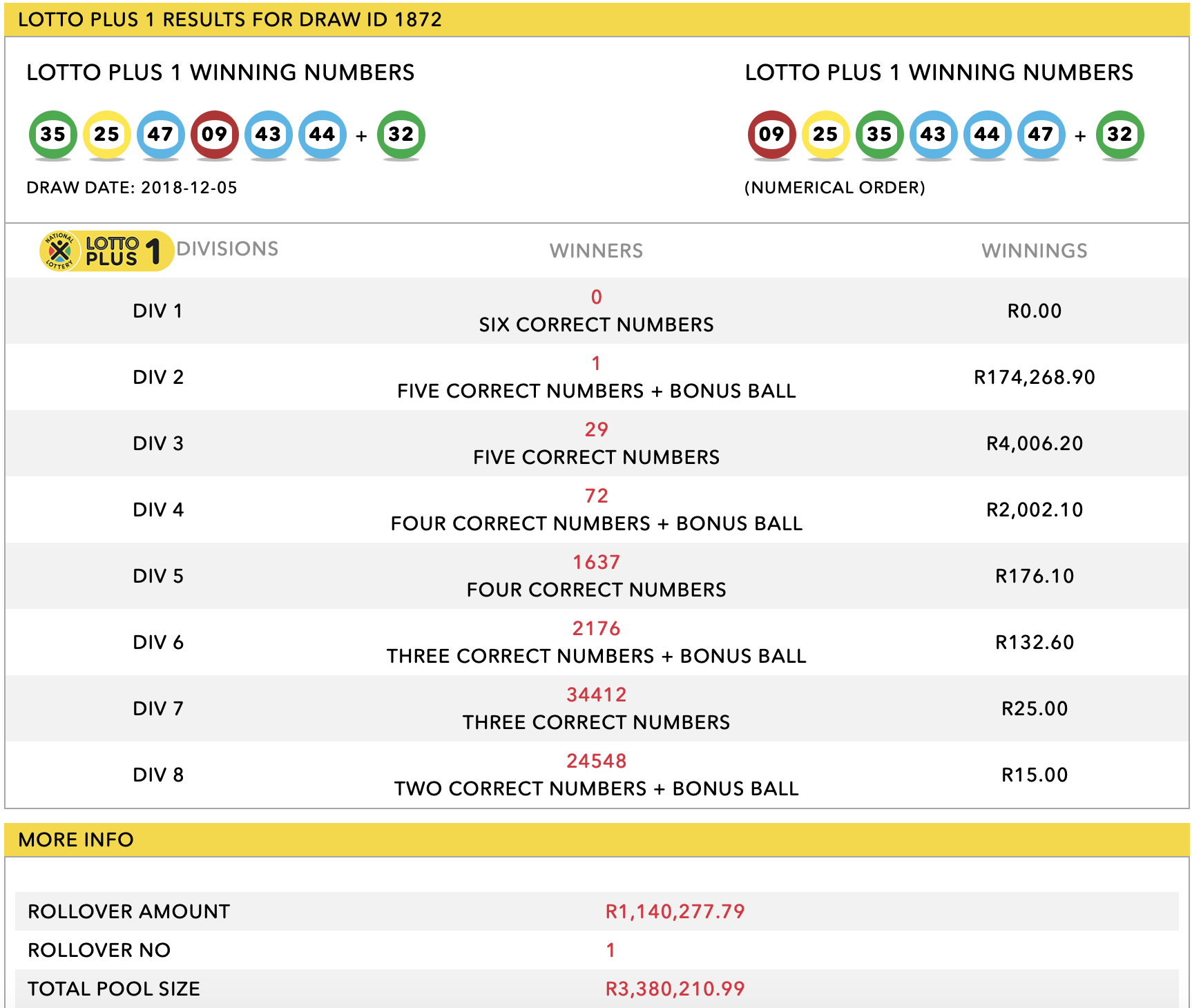 Lotto Results Check Lotto Plus 1 And Lotto Plus 2 Numbers
May 03, 2025
Lotto Results Check Lotto Plus 1 And Lotto Plus 2 Numbers
May 03, 2025 -
 Chinese Maritime Activity Off Sydney Coast A New Normal
May 03, 2025
Chinese Maritime Activity Off Sydney Coast A New Normal
May 03, 2025 -
 Doctor Who Actor Backlash Proves Shows Relevance
May 03, 2025
Doctor Who Actor Backlash Proves Shows Relevance
May 03, 2025
Latest Posts
-
 Shkhsyat Krwyt Mthyrt Lljdl 30 Asma Krhthm Aljmahyr Mwqe Bkra
May 03, 2025
Shkhsyat Krwyt Mthyrt Lljdl 30 Asma Krhthm Aljmahyr Mwqe Bkra
May 03, 2025 -
 Akthr 30 Ryadya Mkrwhyn Mn Qbl Jmahyr Krt Alqdm Bhsb Mwqe Bkra
May 03, 2025
Akthr 30 Ryadya Mkrwhyn Mn Qbl Jmahyr Krt Alqdm Bhsb Mwqe Bkra
May 03, 2025 -
 Akthr 30 Shkhsyt Mkrwht Fy Tarykh Krt Alqdm Mn Hm Aedae Aljmahyr Mwqe Bkra
May 03, 2025
Akthr 30 Shkhsyt Mkrwht Fy Tarykh Krt Alqdm Mn Hm Aedae Aljmahyr Mwqe Bkra
May 03, 2025 -
 Mwqe Bkra Akthr 30 Shkhsyt Krwyt Mkrwht Mn Aljmahyr
May 03, 2025
Mwqe Bkra Akthr 30 Shkhsyt Krwyt Mkrwht Mn Aljmahyr
May 03, 2025 -
 Latest Liverpool News Updates On Frimpong And Elliott
May 03, 2025
Latest Liverpool News Updates On Frimpong And Elliott
May 03, 2025
