Office365 Executive Email Compromise: Millions In Losses Reported
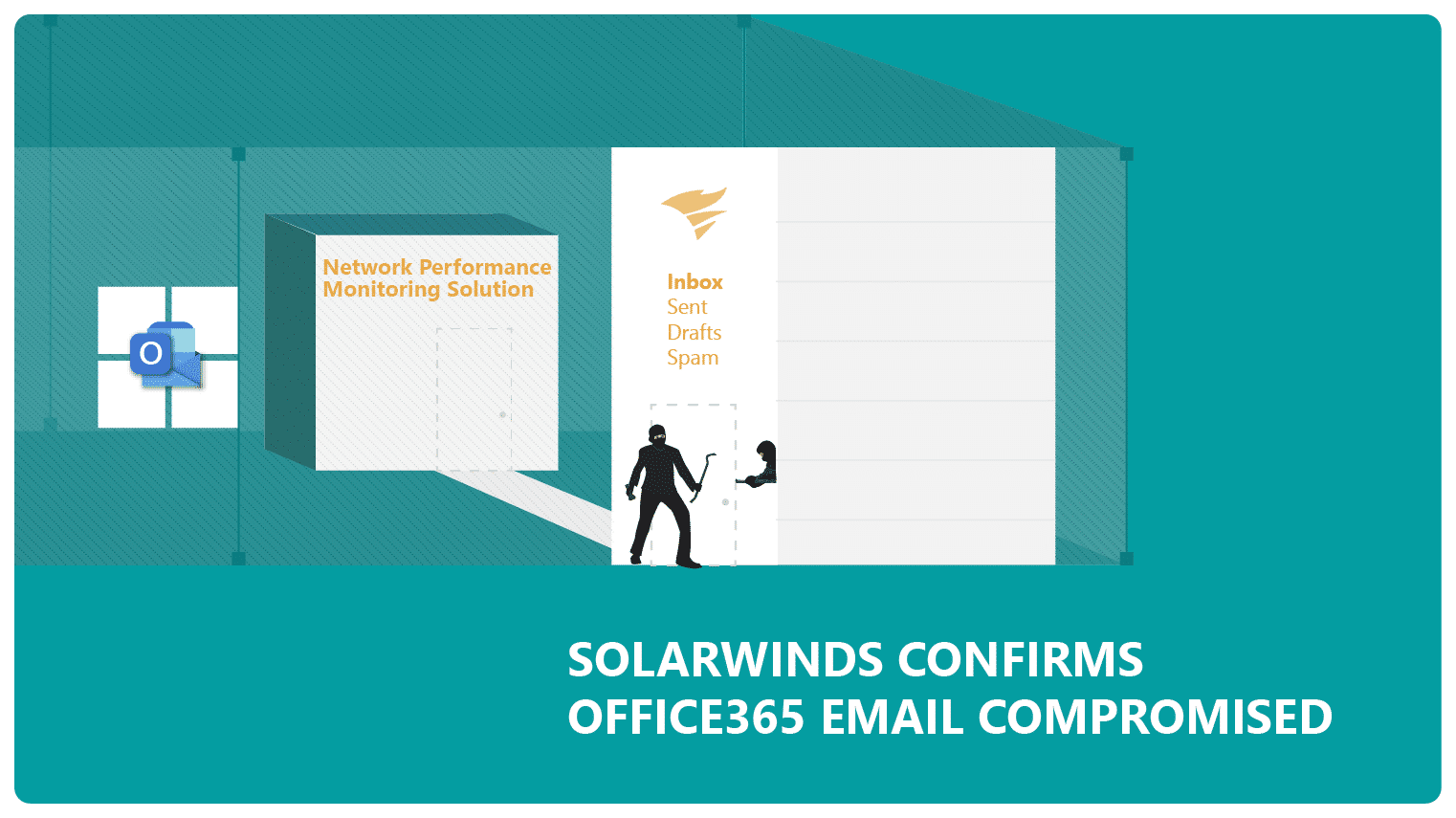
Table of Contents
Understanding Office365 Executive Email Compromise (EEC)
Office365 executive email compromise leverages various techniques to deceive executives and gain unauthorized access to sensitive information and financial accounts. Attackers primarily employ phishing, spear phishing, and whaling—highly targeted attacks designed to appear legitimate.
These attacks often gain access through:
- Compromised Credentials: Attackers may use stolen passwords or exploit weak passwords to gain access to email accounts.
- Social Engineering: This involves manipulating individuals into divulging confidential information or performing actions that compromise security.
- Office365 Vulnerabilities: While less common, attackers may exploit vulnerabilities in the Office365 platform itself to gain unauthorized access.
Common attack vectors targeting executives include:
- Fake Invoices: Emails mimicking legitimate invoices requesting immediate payment.
- Urgent Requests for Wire Transfers: Emails demanding urgent funds transfers under false pretenses.
- Impersonation of Senior Management: Emails appearing to originate from a superior, requesting sensitive data or actions.
- Requests for Sensitive Information: Emails requesting confidential information such as passwords, account details, or personally identifiable information (PII).
Successful EEC attacks result in substantial financial losses, from fraudulent wire transfers to intellectual property theft. The reputational damage can be equally devastating, impacting investor confidence and customer loyalty.
Recognizing the Signs of an Office365 Executive Email Compromise
Identifying suspicious emails is crucial in preventing an EEC attack. Be wary of emails with:
- Suspicious Sender Addresses: Check for slight variations in email addresses or unfamiliar domains.
- Poor Grammar and Spelling: Legitimate communications from executives typically have professional formatting.
- Urgent or Unusual Requests: Be cautious of requests for immediate action or unusual financial transactions.
- Suspicious Attachments or Links: Avoid opening attachments or clicking links from unknown or untrusted sources.
Email authentication protocols like SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting & Conformance) are critical for verifying email authenticity and preventing spoofing. Implementing and properly configuring these protocols is a fundamental step in mitigating EEC risks.
Unusual activity within your organization also signals potential compromise:
- Unexpected Wire Transfers: Monitor financial accounts closely for unauthorized transactions.
- Unusual Login Attempts: Track login attempts from unfamiliar locations or devices.
- Changes in Account Permissions: Regularly review access permissions to ensure no unauthorized changes have been made.
Finally, robust employee training and awareness programs are essential. Regular phishing simulations and security awareness training help employees identify and report suspicious emails and activities.
Protecting Your Organization from Office365 Executive Email Compromise
Implementing strong security measures is paramount in preventing Office365 executive email compromise. Key strategies include:
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, significantly reducing the risk of unauthorized access even if credentials are compromised.
- Robust Security Policies and Procedures: Establish clear policies for password management, access control, and data handling. Implement strong access control lists (ACLs) to limit access to sensitive data.
- Advanced Threat Protection: Utilize Office365's advanced threat protection features to detect and block malicious emails and attachments.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify vulnerabilities and strengthen your defenses.
Further proactive measures include:
- Employee Training on Phishing Awareness: Regular training significantly improves employee ability to identify and report phishing attempts.
- Regular Password Changes: Enforce regular password changes and use strong, unique passwords.
- Email Filtering and Security Tools: Employ robust email filtering and security tools beyond the basic Office365 features.
- Incident Response Planning: Develop a comprehensive incident response plan to guide actions in case of a security breach.
Employing dedicated email security solutions beyond the standard Office365 features enhances protection against advanced persistent threats.
Responding to an Office365 Executive Email Compromise Incident
A swift and decisive response is critical if an EEC incident occurs. Follow these steps:
- Immediate Action: Immediately isolate compromised accounts and prevent further damage.
- Contain the Breach: Take steps to contain the breach and prevent further compromise of systems and data.
- Report to Authorities: Report the incident to relevant authorities, such as law enforcement and data protection agencies.
- Comprehensive Incident Response Plan: A well-defined incident response plan provides a structured approach to handling the situation effectively.
- Forensic Investigation and Recovery: Conduct a thorough forensic investigation to identify the extent of the breach and implement recovery procedures.
Key actions to take include:
- Isolate compromised accounts: Disable access to prevent further unauthorized activity.
- Change passwords: Change all affected passwords immediately.
- Review financial transactions: Thoroughly review recent financial transactions for any unauthorized activity.
- Contact law enforcement: Report the incident to the appropriate law enforcement agencies.
- Conduct a thorough internal investigation: Investigate the incident thoroughly to determine the root cause and implement preventative measures.
Conclusion: Protecting Against Office365 Executive Email Compromise
Office365 executive email compromise poses a significant threat to organizations, resulting in substantial financial and reputational losses. Recognizing the signs of a potential attack, implementing robust security measures, and having a well-defined incident response plan are crucial for mitigating this risk. Proactive steps such as multi-factor authentication, employee training, regular security audits, and the use of advanced threat protection solutions are essential to safeguard your organization. Don't become another statistic. Protect your organization from costly Office365 executive email compromise today by implementing the security measures discussed in this article.

Featured Posts
-
 2024 Nba Playoffs Boston Celtics Game Schedule Vs Orlando Magic
May 06, 2025
2024 Nba Playoffs Boston Celtics Game Schedule Vs Orlando Magic
May 06, 2025 -
 Celtics Vs Knicks Live Stream Tv Channel And How To Watch
May 06, 2025
Celtics Vs Knicks Live Stream Tv Channel And How To Watch
May 06, 2025 -
 Examining Trumps Response Regarding Constitutional Obligations
May 06, 2025
Examining Trumps Response Regarding Constitutional Obligations
May 06, 2025 -
 Mindy Kalings Weight Loss A New Look At The Series Premiere
May 06, 2025
Mindy Kalings Weight Loss A New Look At The Series Premiere
May 06, 2025 -
 Mindy Kalings Transformation Slim Figure Stuns At Premiere
May 06, 2025
Mindy Kalings Transformation Slim Figure Stuns At Premiere
May 06, 2025
Latest Posts
-
 Ddg Unleashes Dont Take My Son A Diss Track Aimed At Halle Bailey
May 06, 2025
Ddg Unleashes Dont Take My Son A Diss Track Aimed At Halle Bailey
May 06, 2025 -
 The Lyrics Of Ddgs Dont Take My Son Explained A Halle Bailey Diss
May 06, 2025
The Lyrics Of Ddgs Dont Take My Son Explained A Halle Bailey Diss
May 06, 2025 -
 Halle Bailey The Target Of Ddgs Dont Take My Son
May 06, 2025
Halle Bailey The Target Of Ddgs Dont Take My Son
May 06, 2025 -
 Ddgs Dont Take My Son Diss Track Sparks Online Debate
May 06, 2025
Ddgs Dont Take My Son Diss Track Sparks Online Debate
May 06, 2025 -
 Ddg Fires Shots At Halle Bailey In Dont Take My Son Diss Track
May 06, 2025
Ddg Fires Shots At Halle Bailey In Dont Take My Son Diss Track
May 06, 2025
