Office365 Security Flaw Costs Executives Millions, FBI Investigation Reveals
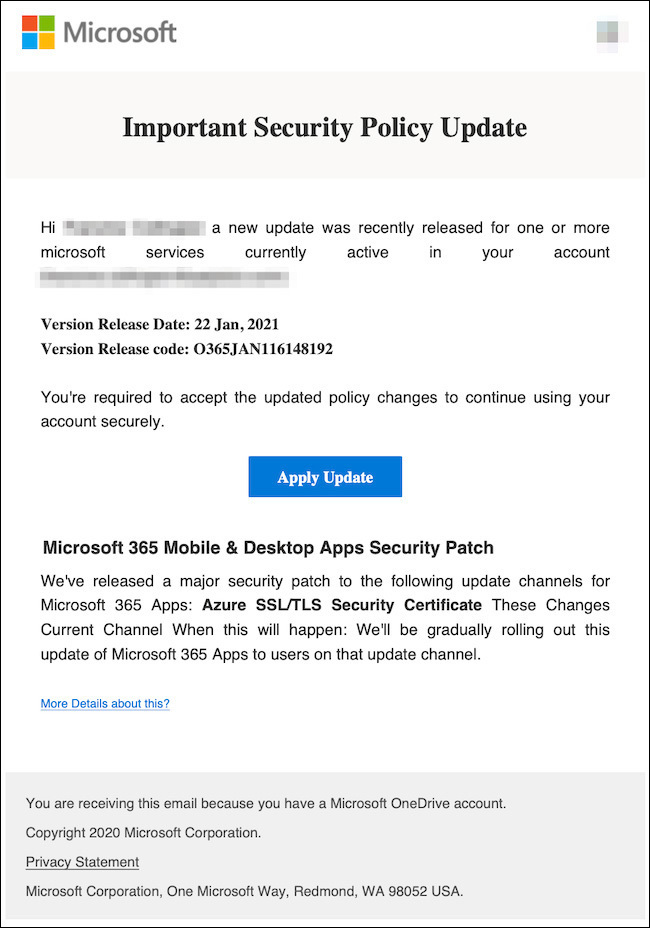
Table of Contents
The Nature of the Office365 Security Flaw Exploited
The Office365 security flaw exploited in this case involved a multifaceted attack leveraging several common vulnerabilities. Attackers primarily targeted weak password security, successfully bypassing authentication mechanisms through sophisticated phishing campaigns and exploiting vulnerabilities in third-party applications integrated with Office365. This allowed for privilege escalation, granting unauthorized access to sensitive data.
The attack vectors employed included:
- Sophisticated Phishing Emails: These emails expertly mimicked legitimate communications from trusted sources, tricking employees into revealing their credentials.
- Malicious Links and Attachments: These led to credential-theft websites or downloaded malware onto employee devices, providing a backdoor into the Office365 environment.
- Exploitation of Third-Party Apps: Attackers targeted vulnerabilities in less secure third-party applications connected to Office365, gaining unauthorized access through these less-protected entry points. This highlights the importance of vetting and regularly reviewing all third-party app permissions.
- Authentication Bypass: Attackers utilized various techniques to circumvent the standard authentication processes, gaining access without needing valid login credentials.
The Scale of the Damage: Financial Losses and Data Breaches
The financial ramifications of this Office365 security flaw are staggering. The FBI investigation indicates that affected executives and their organizations suffered millions of dollars in losses. The precise figures remain confidential due to the ongoing investigation, but the scale of the damage is undeniable.
The data breaches resulted in the compromise of:
- Financial Records: Bank account details, transaction histories, and other sensitive financial information were accessed.
- Intellectual Property: Confidential research, proprietary designs, and trade secrets were stolen, potentially causing irreparable harm.
- Customer Data: Personal information of customers, including addresses, contact details, and purchase histories, was exposed, leading to potential identity theft and reputational damage.
- Sensitive Employee Information: Payroll data, employee records, and other confidential HR information were compromised.
The consequences extend far beyond the direct financial losses, encompassing:
- Direct Financial Losses: Ransom payments, legal fees, and the costs associated with data recovery and forensic investigations.
- Indirect Costs: Business disruption, loss of productivity, and the time and resources spent on damage control and remediation.
- Reputational Damage and Loss of Customer Confidence: The breach severely damaged the reputation of affected companies, leading to loss of customer trust and potential long-term economic repercussions.
The FBI Investigation: Key Findings and Actions Taken
The FBI investigation into the Office365 security flaw is ongoing. Initial findings reveal a sophisticated, coordinated attack targeting multiple organizations. The investigation focused on identifying the perpetrators, tracing the attack vectors, and assisting victims in recovering compromised data. Key actions taken by the FBI include:
- Identifying Compromised Systems: The FBI worked to locate and secure affected systems to prevent further data breaches.
- Assisting Victims in Recovering Data: The FBI provided crucial support to victims in recovering their lost data and mitigating the impact of the breach.
- Tracking Down Perpetrators: The FBI launched a comprehensive investigation to identify and prosecute those responsible for the attack.
- Issuing Public Warnings about the Vulnerability: The FBI issued public warnings about the Office365 security flaw, urging organizations to strengthen their security measures.
Preventing Future Office365 Security Flaws: Best Practices for Executives
Protecting your organization from similar Office365 security flaws requires a multi-layered approach. Executives must prioritize proactive security measures to prevent devastating breaches. Here are some crucial steps:
- Implement Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring multiple forms of authentication to access accounts, significantly reducing the risk of unauthorized access.
- Regularly Update Software and Patches: Keep all software, including Office365 applications and operating systems, up to date with the latest security patches to address known vulnerabilities.
- Conduct Security Awareness Training for Employees: Educate employees about phishing scams, malicious links, and other social engineering tactics to prevent them from falling victim to attacks.
- Enforce Strong Password Policies: Implement robust password policies that require strong, unique passwords and regular password changes.
- Utilize Advanced Threat Protection Tools: Employ advanced threat protection solutions to detect and prevent malicious activity within your Office365 environment.
- Regular Security Audits: Conduct regular security audits and penetration testing to identify and address potential vulnerabilities.
Conclusion: Protecting Your Business from Office365 Security Flaws
The recent Office365 security flaw exposed by the FBI investigation serves as a stark reminder of the critical importance of robust cybersecurity measures. The financial losses and reputational damage suffered by affected organizations highlight the devastating consequences of neglecting security best practices. The FBI's response underscores the seriousness of the threat. By implementing the recommended preventative measures – including MFA, regular software updates, employee training, strong password policies, advanced threat protection, and regular security audits – executives can significantly reduce their risk of experiencing a similar Office365 security breach. Don't let an Office365 security flaw cost your business millions – act now! Implement these crucial security measures and protect your organization from the devastating consequences of a potential cyberattack.

Featured Posts
-
 2025 Streaming Wars Fox And Espn Enter The Arena
May 05, 2025
2025 Streaming Wars Fox And Espn Enter The Arena
May 05, 2025 -
 Police Investigating Fatal Collision Near Yellowstone Seven Dead
May 05, 2025
Police Investigating Fatal Collision Near Yellowstone Seven Dead
May 05, 2025 -
 Fox Sports Indy Car Coverage What To Expect This Season
May 05, 2025
Fox Sports Indy Car Coverage What To Expect This Season
May 05, 2025 -
 Apo Main Event Nelson Dong Secures A 390 000 Prize
May 05, 2025
Apo Main Event Nelson Dong Secures A 390 000 Prize
May 05, 2025 -
 Ufc 314 Volkanovski Lopes Fight Early Betting Odds And Predictions
May 05, 2025
Ufc 314 Volkanovski Lopes Fight Early Betting Odds And Predictions
May 05, 2025
Latest Posts
-
 Knjiga Drvo I Koncert Gibonni U Subotici
May 05, 2025
Knjiga Drvo I Koncert Gibonni U Subotici
May 05, 2025 -
 Gibonni Nova Knjiga Drvo I Koncert U Sinagogi Subotica
May 05, 2025
Gibonni Nova Knjiga Drvo I Koncert U Sinagogi Subotica
May 05, 2025 -
 The Enduring Appeal Of Fleetwood Macs Top Songs
May 05, 2025
The Enduring Appeal Of Fleetwood Macs Top Songs
May 05, 2025 -
 Fleetwood Macs Biggest Hits A Testament To Enduring Popularity
May 05, 2025
Fleetwood Macs Biggest Hits A Testament To Enduring Popularity
May 05, 2025 -
 96 1 The Rocket A Deep Dive Into Peter Greens Fleetwood Mac Era
May 05, 2025
96 1 The Rocket A Deep Dive Into Peter Greens Fleetwood Mac Era
May 05, 2025
