Office365 Security Flaw: Millions Lost In Executive Email Breach
Table of Contents
Understanding the Office365 Security Flaw Exploited
The Weakness in Authentication and Authorization
The core vulnerability exploited in this Office365 security breach stemmed from weaknesses in authentication and authorization processes. Attackers leveraged a combination of sophisticated techniques to bypass security measures, primarily focusing on human error and inadequate security protocols.
- Phishing Attacks: Attackers sent highly targeted spear-phishing emails designed to mimic legitimate communications from trusted sources. These emails often contained malicious links or attachments designed to deliver malware or steal credentials.
- Weak Passwords: Many executives used easily guessable passwords or reused passwords across multiple accounts. This significantly reduced the barrier to entry for attackers.
- Lack of Multi-Factor Authentication (MFA): The absence of MFA allowed attackers to gain access to accounts even if they successfully obtained login credentials through phishing or other means. MFA adds an extra layer of security, requiring a second form of verification beyond a password.
- Account Takeover: Once credentials were compromised, attackers quickly gained control of executive email accounts, granting them access to sensitive information and communication channels.
The Impact of the Executive Email Breach
Financial Losses and Reputational Damage
The consequences of this Office365 security breach were severe and far-reaching. Millions of dollars were stolen through various fraudulent activities.
- Wire Fraud: Attackers used compromised accounts to initiate fraudulent wire transfers, diverting funds to offshore accounts.
- Ransomware Payments: In some cases, organizations were forced to pay substantial ransoms to regain access to their data after ransomware attacks launched from compromised accounts.
- Reputational Damage: The breach significantly impacted the reputation of affected organizations, eroding customer trust and potentially leading to legal repercussions and financial penalties. Loss of investor confidence also resulted in significant market value decreases.
How Attackers Executed the Breach
The Attack Methodology
The attack followed a well-defined pattern:
- Initial Contact: Attackers sent sophisticated spear-phishing emails, carefully tailored to the target's organization and role.
- Credential Harvesting: Victims, falling prey to the phishing attempts, unwittingly revealed their login credentials.
- Account Compromise: Attackers used the stolen credentials to gain unauthorized access to executive email accounts.
- Data Exfiltration: Sensitive information, including financial data and internal communications, was extracted.
- Fraudulent Activity: Attackers executed wire transfers, ransomware deployments, or other fraudulent activities using the compromised accounts.
Preventing Future Office365 Security Breaches
Best Practices for Enhanced Security
Proactive measures are vital to prevent similar Office365 security breaches. Here are some crucial steps:
- Strong Password Policies: Enforce complex, unique passwords and regularly update them. Password managers can assist with this.
- Multi-Factor Authentication (MFA): Mandate MFA for all Office365 accounts. This adds a significant layer of protection against unauthorized access.
- Security Awareness Training: Regularly educate employees about phishing scams, social engineering tactics, and safe email practices. Simulate phishing attacks to test awareness levels.
- Advanced Security Solutions: Implement email security gateways and intrusion detection systems to filter malicious emails and detect suspicious activity.
- Data Loss Prevention (DLP): Employ DLP measures to monitor and prevent sensitive data from leaving the organization's network.
- Regular Security Audits: Conduct periodic security assessments to identify and address vulnerabilities in your Office365 environment.
Conclusion: Protecting Your Organization from Office365 Security Threats
This Office365 security breach serves as a stark reminder of the critical need for robust cybersecurity practices. The vulnerability exploited highlights the devastating impact of inadequate authentication, authorization, and a lack of employee awareness. By implementing strong password policies, mandating multi-factor authentication, investing in advanced security solutions, and providing comprehensive security awareness training, organizations can significantly reduce their risk of falling victim to similar attacks. Don't become another victim of an Office365 security breach. Implement strong security measures today to protect your organization and its valuable data. Improve your Office365 security now and safeguard your future.

Featured Posts
-
 Pierre Poilievres Election Defeat A Shock For Canadas Conservatives
May 01, 2025
Pierre Poilievres Election Defeat A Shock For Canadas Conservatives
May 01, 2025 -
 Klas Recognizes Nrc Health As The Leading Healthcare Experience Management Provider
May 01, 2025
Klas Recognizes Nrc Health As The Leading Healthcare Experience Management Provider
May 01, 2025 -
 Nuclear Litigation Key Legal Issues And Recent Developments
May 01, 2025
Nuclear Litigation Key Legal Issues And Recent Developments
May 01, 2025 -
 Remembering Ted Kotcheff Director Of Rambo First Blood 1982
May 01, 2025
Remembering Ted Kotcheff Director Of Rambo First Blood 1982
May 01, 2025 -
 Alteawn Tezyz Alslslt Almmyzt Fy Mwajht Thdyat Alshbab
May 01, 2025
Alteawn Tezyz Alslslt Almmyzt Fy Mwajht Thdyat Alshbab
May 01, 2025
Latest Posts
-
 Nws Kentucky Get Ready For Severe Weather Awareness Week
May 01, 2025
Nws Kentucky Get Ready For Severe Weather Awareness Week
May 01, 2025 -
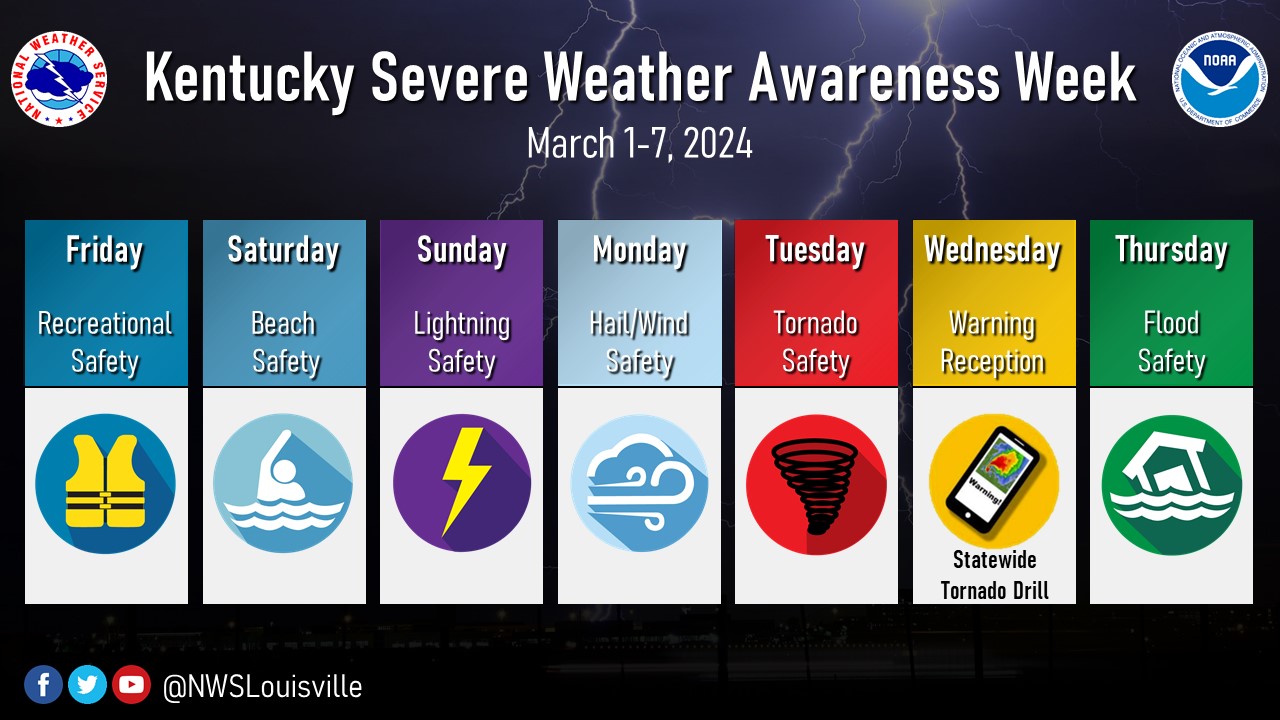 Kentucky Severe Weather Nws Readiness For Awareness Week
May 01, 2025
Kentucky Severe Weather Nws Readiness For Awareness Week
May 01, 2025 -
 Louisville Mail Delivery Issues Union Offers Positive Outlook
May 01, 2025
Louisville Mail Delivery Issues Union Offers Positive Outlook
May 01, 2025 -
 National Weather Service Prepares For Kentuckys Severe Weather Awareness Week
May 01, 2025
National Weather Service Prepares For Kentuckys Severe Weather Awareness Week
May 01, 2025 -
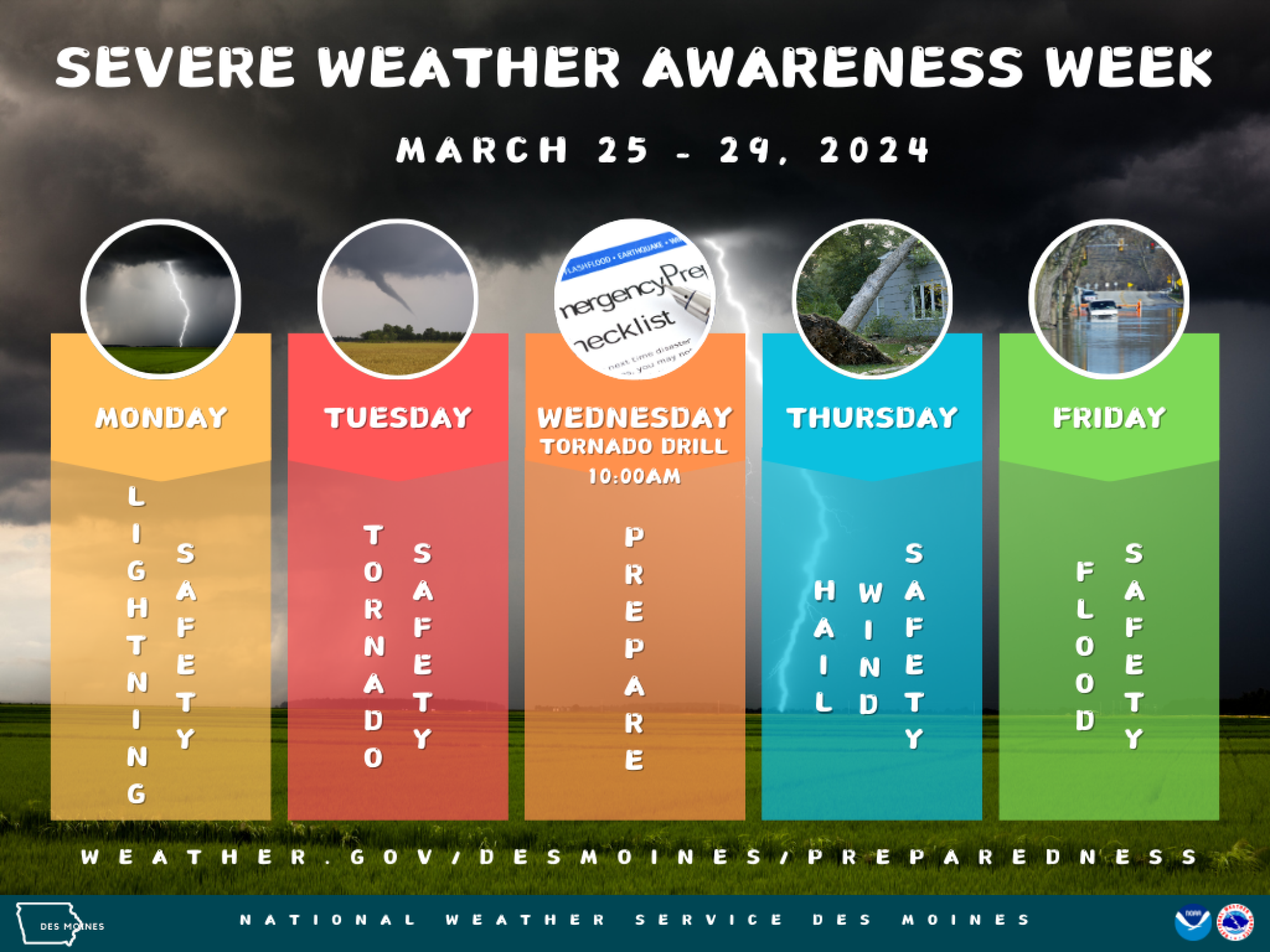 Kentucky Severe Weather Awareness Week Nws Preparedness Plans
May 01, 2025
Kentucky Severe Weather Awareness Week Nws Preparedness Plans
May 01, 2025
