Secure Data Transfer: Protecting Your Information
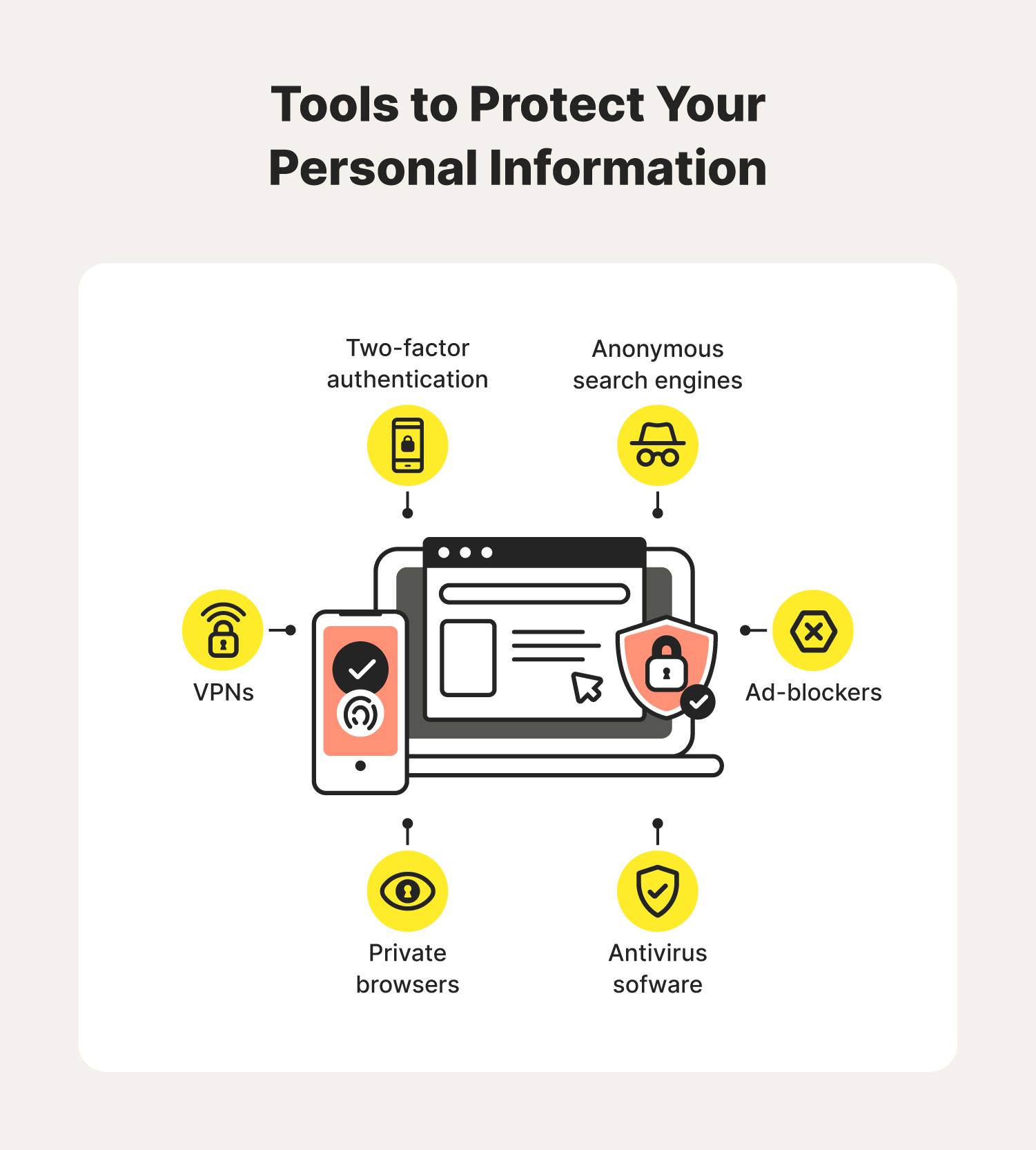
Table of Contents
Understanding the Risks of Insecure Data Transfer
Data Breaches and Their Consequences
Data breaches can occur through various means, including phishing attacks, malware infections, and exploitation of software vulnerabilities. The consequences can be devastating, leading to significant financial losses, reputational damage, and hefty legal penalties. For example, a single breach can cost a company millions of dollars in remediation, legal fees, and lost business.
- Examples of real-world data breaches and their costs: The Equifax breach of 2017 compromised 147 million individuals' personal information, costing the company over $700 million. The Yahoo! data breaches in 2013 and 2014 exposed billions of user accounts, resulting in significant reputational damage and legal settlements.
- Types of data vulnerable in transfer: Personally Identifiable Information (PII), financial data (credit card numbers, bank account details), intellectual property, and trade secrets are all highly sensitive and valuable targets for cybercriminals.
Compliance Regulations and Data Protection Laws
Numerous regulations and laws mandate secure data handling and transfer. Non-compliance can result in substantial fines and legal repercussions. Key regulations include:
- Key requirements of these regulations regarding data transfer: Regulations like GDPR (General Data Protection Regulation), CCPA (California Consumer Privacy Act), and HIPAA (Health Insurance Portability and Accountability Act) require organizations to implement appropriate technical and organizational measures to ensure the security of personal data during transfer. This often involves encryption and secure protocols.
- Penalties for non-compliance: Penalties for violating these regulations can range from millions of dollars in fines to legal action and reputational damage.
Methods for Secure Data Transfer
Encryption Techniques
Encryption is a fundamental aspect of secure data transfer. It transforms readable data (plaintext) into an unreadable format (ciphertext), protecting it from unauthorized access. Different encryption methods exist:
- Examples of encryption protocols (TLS, SSL, PGP): TLS (Transport Layer Security) and its predecessor SSL (Secure Sockets Layer) are widely used for securing web traffic. PGP (Pretty Good Privacy) is commonly used for encrypting emails and files.
- Strengths and weaknesses of each encryption method: Symmetric encryption uses the same key for encryption and decryption, offering speed but requiring secure key exchange. Asymmetric encryption uses separate keys, enhancing security but being slower. End-to-end encryption ensures only the sender and recipient can access the data.
Secure Protocols and Technologies
Several secure protocols facilitate secure data transfer:
- Comparison of different protocols and their suitability for various data transfer scenarios: HTTPS (for web traffic), SFTP (for secure file transfer over SSH), FTPS (for secure file transfer over FTP), and VPNs (for creating secure connections) each offer varying levels of security and are suited for different applications.
- How to choose the right protocol for your needs: The choice depends on factors like the sensitivity of the data, the required level of security, and the type of transfer (file transfer, web browsing, email).
Virtual Private Networks (VPNs)
VPNs create a secure, encrypted connection between your device and a server, masking your IP address and encrypting your data. This enhances your privacy and security during data transfer:
- Different types of VPNs (personal, business): Personal VPNs are used for individual protection, while business VPNs are designed for secure internal communication and remote access.
- Benefits of using a VPN for data protection: VPNs protect data from eavesdropping, enhance anonymity, and bypass geographical restrictions.
Best Practices for Secure Data Transfer
Strong Password Management
Strong, unique passwords are essential for secure data transfer:
- Best practices for password creation and storage: Use long, complex passwords, change them regularly, and use a password manager to store them securely.
- Risks of weak or reused passwords: Weak passwords make your data vulnerable to brute-force attacks and credential stuffing.
Regular Software Updates
Keeping software and operating systems updated is critical:
- How to enable automatic updates: Most operating systems and applications offer automatic update features.
- The dangers of outdated software: Outdated software contains known vulnerabilities that cybercriminals can exploit.
Two-Factor Authentication (2FA)
2FA adds an extra layer of security, requiring a second form of verification beyond a password:
- Different types of 2FA methods: Common methods include one-time codes via SMS, authentication apps (like Google Authenticator), and security keys.
- Benefits and implementation of 2FA: 2FA significantly reduces the risk of unauthorized access even if your password is compromised.
Employee Training and Awareness
Educating employees about data security is crucial:
- Topics to cover in employee training: Training should cover phishing awareness, password security, secure browsing habits, and recognizing social engineering tactics.
- Importance of security awareness programs: Regular security awareness training reinforces good security practices and reduces the risk of human error.
Conclusion
By implementing strong encryption, utilizing secure protocols like HTTPS, SFTP, and VPNs, practicing good password hygiene, and keeping software updated, you can significantly reduce the risks associated with data transfer. Prioritize secure data transfer practices to safeguard your valuable information. Implement the strategies outlined above to bolster your organization's cybersecurity posture and protect against costly data breaches. For a comprehensive security assessment, consider consulting with a cybersecurity expert.

Featured Posts
-
 Jayson Tatums Forgotten Potential Colin Cowherds Perspective
May 08, 2025
Jayson Tatums Forgotten Potential Colin Cowherds Perspective
May 08, 2025 -
 Star Wars New Tv Show To Reveal The Origin Of A Rogue One Hero
May 08, 2025
Star Wars New Tv Show To Reveal The Origin Of A Rogue One Hero
May 08, 2025 -
 Us Antisemitism Probe Investigates Anti Boeing Activity On Seattle Campus
May 08, 2025
Us Antisemitism Probe Investigates Anti Boeing Activity On Seattle Campus
May 08, 2025 -
 Lotto Draw Results Check The Latest Numbers For Lotto Plus 1 And 2
May 08, 2025
Lotto Draw Results Check The Latest Numbers For Lotto Plus 1 And 2
May 08, 2025 -
 Dwp Benefit Changes Impact And Support For Affected Claimants
May 08, 2025
Dwp Benefit Changes Impact And Support For Affected Claimants
May 08, 2025
