T-Mobile Penalty: $16 Million For Repeated Data Breaches
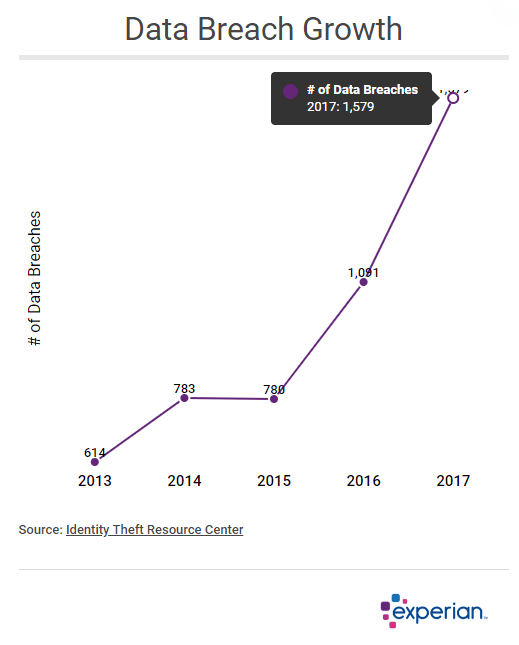
Table of Contents
Details of the T-Mobile Data Breaches
The T-Mobile data breaches weren't isolated incidents; they represent a pattern of failures in data security. Understanding the timeline and the types of data compromised is crucial to grasping the severity of the situation.
T-Mobile Data Breach Timeline: Customer Data Compromised
The timeline of T-Mobile data breaches reveals a concerning trend:
- 2021: A massive breach exposed personal information of over 50 million people, including names, addresses, Social Security numbers, and driver's license information. This T-Mobile data breach highlighted significant vulnerabilities in their systems.
- 2022: Further breaches occurred, impacting additional millions of customers and showcasing the lack of effective remediation following the 2021 incident. The exact number of affected customers in these subsequent breaches varies depending on the source and specifics of each event, but millions more were affected.
- Ongoing: While the most significant breaches occurred in 2021 and 2022, the ongoing nature of security concerns at T-Mobile indicates a systemic problem that requires comprehensive solutions.
Types of Data Compromised: Sensitive Data and Personal Information Breach
The compromised data included highly sensitive personal information:
- Personal Information: Names, addresses, dates of birth, and Social Security numbers were exposed, making affected customers vulnerable to identity theft.
- Financial Data: While the extent of financial data exposure varied across breaches, some instances included sensitive financial information, increasing the risk of fraud.
- Location Data: In some cases, location data was also compromised, raising privacy concerns and potential for misuse. This highlights the broad scope of the sensitive data at risk within T-Mobile systems.
Root Causes of the Breaches: Data Security Failures and Cybersecurity Vulnerabilities
The repeated breaches point to systemic failures in T-Mobile's data security infrastructure and practices:
- Inadequate Security Measures: Insufficient security protocols and outdated technology left T-Mobile vulnerable to attacks.
- Insufficient Employee Training: Lack of proper employee training on cybersecurity best practices contributed to vulnerabilities.
- Outdated Systems: Reliance on legacy systems without adequate updates increased the risk of exploitation. This points to a larger issue within the company culture and its approach to cybersecurity.
The $16 Million FCC Penalty
The $16 million FCC penalty reflects the gravity of T-Mobile's repeated failures in protecting consumer data.
FCC's Rationale: Regulatory Action and Data Breach Penalties
The FCC's action was based on several factors:
- Severity of Breaches: The sheer number of affected customers and the sensitivity of the compromised data.
- Repeated Nature: The pattern of breaches demonstrated a lack of proactive measures to address vulnerabilities.
- Failure to Comply: T-Mobile's failure to adhere to adequate data security standards and regulatory requirements.
Legal Implications: Consumer Lawsuits and Class-Action Lawsuit
The penalty is not the only consequence. T-Mobile faces potential legal ramifications, including:
- Consumer Lawsuits: Individual customers may pursue legal action to recover damages resulting from the breaches.
- Class-Action Lawsuit: A class-action lawsuit could be filed on behalf of a large group of affected customers.
Impact on T-Mobile's Reputation: Brand Reputation and Customer Trust
The breaches and the subsequent penalty have severely damaged T-Mobile's reputation:
- Loss of Customer Trust: Many customers lost faith in T-Mobile's ability to protect their sensitive information.
- Negative Publicity: The negative press surrounding the breaches significantly impacted T-Mobile's brand image.
Lessons Learned and Future Implications
The T-Mobile case provides critical lessons for improving data security and highlights the increasing regulatory scrutiny faced by telecom companies.
Best Practices for Data Security: Data Security Best Practices and Cybersecurity Measures
Companies must implement robust data security measures, including:
- Multi-factor Authentication: Adding an extra layer of security to access accounts.
- Employee Security Training: Regular and comprehensive training on cybersecurity best practices.
- Regular Security Audits: Conducting frequent audits to identify and address vulnerabilities.
- Encryption: Encrypting sensitive data both in transit and at rest.
- Robust Intrusion Detection Systems: Implementing systems to detect and respond to security threats.
Regulatory Scrutiny of Telecom Companies: Regulatory Compliance and Data Security Regulations
The increased regulatory scrutiny means telecom companies must prioritize data security compliance:
- Stringent Regulations: Expect stricter regulations and penalties for data breaches.
- Proactive Measures: Companies must proactively address vulnerabilities and implement robust security protocols.
Consumer Awareness and Data Privacy: Consumer Data Privacy and Protecting Personal Data
Consumers also play a vital role in protecting their personal data:
- Online Security Awareness: Educating oneself about online threats and best practices for protecting personal information.
- Data Privacy: Understanding privacy policies and exercising caution when sharing personal data online.
Conclusion
The $16 million penalty imposed on T-Mobile serves as a stark reminder of the critical importance of robust data security in the telecom industry. The repeated data breaches highlight the severe consequences of inadequate security measures and the need for proactive steps to protect consumer data. The lessons learned should prompt both companies and consumers to prioritize data security. To learn more about protecting your personal data online and demanding better data security practices from telecom companies, explore resources on data security and privacy. Preventing future T-Mobile data breaches, or similar incidents at other companies, requires a concerted effort from all stakeholders.

Featured Posts
-
 Tanner Bibees First Pitch Homer Guardians Rally Defeats Yankees
May 01, 2025
Tanner Bibees First Pitch Homer Guardians Rally Defeats Yankees
May 01, 2025 -
 Early Death Risk Doctor Identifies The Single Worst Food Even Worse Than Smoking
May 01, 2025
Early Death Risk Doctor Identifies The Single Worst Food Even Worse Than Smoking
May 01, 2025 -
 Zdravkova Prva Ljubav Prica Iza Pesme Kad Sam Se Vratio
May 01, 2025
Zdravkova Prva Ljubav Prica Iza Pesme Kad Sam Se Vratio
May 01, 2025 -
 Boulangerie Normande Un Cadeau Chocolate Pour Le Premier Bebe De L Annee
May 01, 2025
Boulangerie Normande Un Cadeau Chocolate Pour Le Premier Bebe De L Annee
May 01, 2025 -
 Warriors Vs Rockets Bet Mgm Bonus Code Rotobg 150 For 150
May 01, 2025
Warriors Vs Rockets Bet Mgm Bonus Code Rotobg 150 For 150
May 01, 2025
Latest Posts
-
 I Pari Sen Zermen Paramenei Stin Euroleague Epivevaiosi Gia Tin Epomeni Sezon
May 01, 2025
I Pari Sen Zermen Paramenei Stin Euroleague Epivevaiosi Gia Tin Epomeni Sezon
May 01, 2025 -
 Will The Portland Trail Blazers Secure A Play In Spot
May 01, 2025
Will The Portland Trail Blazers Secure A Play In Spot
May 01, 2025 -
 Dagskra Bestu Deildarinnar Hvad Er I Bodi I Dag
May 01, 2025
Dagskra Bestu Deildarinnar Hvad Er I Bodi I Dag
May 01, 2025 -
 Chilean Migrants Charged In Series Of Nfl Player Robberies
May 01, 2025
Chilean Migrants Charged In Series Of Nfl Player Robberies
May 01, 2025 -
 Portland Trail Blazers Play In Tournament Chances A Realistic Assessment
May 01, 2025
Portland Trail Blazers Play In Tournament Chances A Realistic Assessment
May 01, 2025
