Exec Office365 Breach: Millions Made From Inbox Hacks, FBI Says
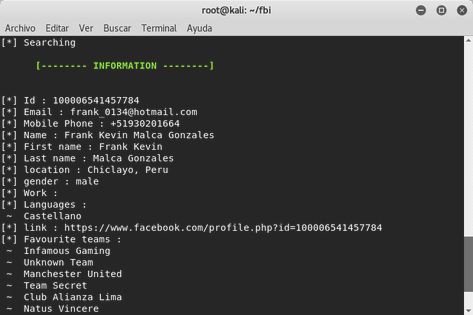
Table of Contents
The Scale of the Office365 Breach Problem
The scale of the Office365 breach problem is alarming. While precise figures from the FBI regarding the total number of breaches remain confidential for investigative reasons, reports indicate a substantial and growing number of incidents resulting in significant financial losses. The FBI's warnings highlight that millions of dollars are lost annually due to data theft and extortion related to compromised Office365 accounts. Although specific company names are generally kept confidential due to ongoing investigations and the sensitivity of the data, the impact is far-reaching. The consequences extend beyond simple financial losses.
- Millions of dollars lost annually due to data theft, ransomware attacks, and extortion.
- Significant reputational damage for affected organizations, leading to loss of customer trust and potential legal repercussions.
- Disruption to business operations due to data breaches, system downtime, and the time-consuming process of recovery.
- Increased insurance premiums for affected businesses as risk assessments rise.
These Office 365 security breaches, impacting email security and causing widespread data breach costs, necessitate a proactive approach to mitigation.
Common Hacking Techniques Used in Office365 Breaches
Hackers employ a range of sophisticated techniques to breach Office365 accounts. These attacks often leverage vulnerabilities in human behavior and system weaknesses.
Phishing Attacks: These remain incredibly effective. Sophisticated phishing emails, often mimicking legitimate communications from trusted sources, trick employees into revealing their login credentials or clicking malicious links. Spear phishing, which targets specific individuals within an organization, is particularly dangerous.
Credential Stuffing and Brute-Force Attacks: Hackers utilize lists of stolen usernames and passwords obtained from other breaches (credential stuffing) or automated tools to try various password combinations (brute-force attacks). Weak passwords make organizations particularly vulnerable.
Exploiting Vulnerabilities: Hackers actively search for and exploit vulnerabilities in Office 365 applications and their integrations with third-party services. Zero-day exploits, which target newly discovered vulnerabilities before patches are available, pose a significant threat.
Here are some specific methods employed:
- Spear phishing emails targeting executives with personalized messages.
- Compromised third-party applications with access to Office365 data.
- Exploitation of zero-day vulnerabilities in Office 365 software and integrations.
- Use of malicious links disguised as legitimate documents or websites.
- Social engineering tactics to manipulate employees into divulging sensitive information.
These methods highlight the importance of robust password security and vigilance against phishing attacks.
Protecting Your Business from Office365 Breaches
Protecting your business from Office365 breaches requires a multi-layered approach combining technical safeguards and employee training.
Multi-Factor Authentication (MFA): Implementing MFA is crucial. This adds an extra layer of security, requiring more than just a password to access accounts, significantly reducing the risk of unauthorized access even if credentials are compromised.
Strong Password Policies: Enforce strong password policies that mandate complex passwords, regular password changes, and the use of password managers. Avoid password reuse across multiple accounts.
Robust Email Security Solutions: Invest in robust email security solutions that include advanced spam filtering, anti-phishing measures, and malware scanning to identify and block malicious emails before they reach employees' inboxes.
Security Audits and Employee Training: Regular security audits identify vulnerabilities in your systems. Invest in comprehensive cybersecurity awareness training programs to educate employees about phishing scams, social engineering tactics, and best practices for online security.
Here are some practical preventative steps:
- Implement MFA for all Office365 accounts.
- Enforce strong password policies and encourage the use of password managers.
- Train employees to identify and report phishing attempts immediately.
- Regularly update software and patches to address known vulnerabilities.
- Conduct regular security audits to identify and address potential weaknesses.
- Segment your network to limit the impact of a potential breach.
By combining these measures, organizations can significantly enhance their Office365 security and minimize their exposure to costly data breaches.
Conclusion
The scale of the Office365 breach problem is undeniable, with hackers exploiting various methods to gain access to sensitive data and inflict significant financial damage on businesses. The common hacking techniques employed, from phishing attacks to the exploitation of vulnerabilities, highlight the need for a proactive and multi-layered security approach. Don't become another statistic. Strengthen your Office365 security today by implementing multi-factor authentication, robust password policies, and comprehensive employee training. Protect your business from the devastating financial consequences of an Office365 breach. For further information on best practices for Office365 security, [link to relevant resource].

Featured Posts
-
 Ai Powered Podcast Creation Turning Repetitive Scatological Documents Into Engaging Content
Apr 22, 2025
Ai Powered Podcast Creation Turning Repetitive Scatological Documents Into Engaging Content
Apr 22, 2025 -
 V Mware Costs To Skyrocket At And T Details 1 050 Price Increase From Broadcom
Apr 22, 2025
V Mware Costs To Skyrocket At And T Details 1 050 Price Increase From Broadcom
Apr 22, 2025 -
 Pope Franciss Legacy The Conclaves Crucial Test
Apr 22, 2025
Pope Franciss Legacy The Conclaves Crucial Test
Apr 22, 2025 -
 Office365 Security Breach Executive Inboxes Targeted Millions In Damages
Apr 22, 2025
Office365 Security Breach Executive Inboxes Targeted Millions In Damages
Apr 22, 2025 -
 The Karen Read Murder Case A Chronological Overview
Apr 22, 2025
The Karen Read Murder Case A Chronological Overview
Apr 22, 2025
Latest Posts
-
 The Masters Aftermath Shane Lowrys Message Of Support For Rory Mc Ilroy
May 12, 2025
The Masters Aftermath Shane Lowrys Message Of Support For Rory Mc Ilroy
May 12, 2025 -
 Lowrys Encouraging Words For Mc Ilroy Post Masters Highlight Their Strong Bond
May 12, 2025
Lowrys Encouraging Words For Mc Ilroy Post Masters Highlight Their Strong Bond
May 12, 2025 -
 Rory Mc Ilroys Zurich Classic Return With Shane Lowry
May 12, 2025
Rory Mc Ilroys Zurich Classic Return With Shane Lowry
May 12, 2025 -
 Mc Ilroy Lowry Team Six Strokes Behind In Zurich Classic Defense
May 12, 2025
Mc Ilroy Lowry Team Six Strokes Behind In Zurich Classic Defense
May 12, 2025 -
 Rory Mc Ilroy And Shane Lowry Face Up Hill Battle In Zurich Classic
May 12, 2025
Rory Mc Ilroy And Shane Lowry Face Up Hill Battle In Zurich Classic
May 12, 2025
