Office365 Security Breach: Executive Inboxes Targeted, Millions In Damages
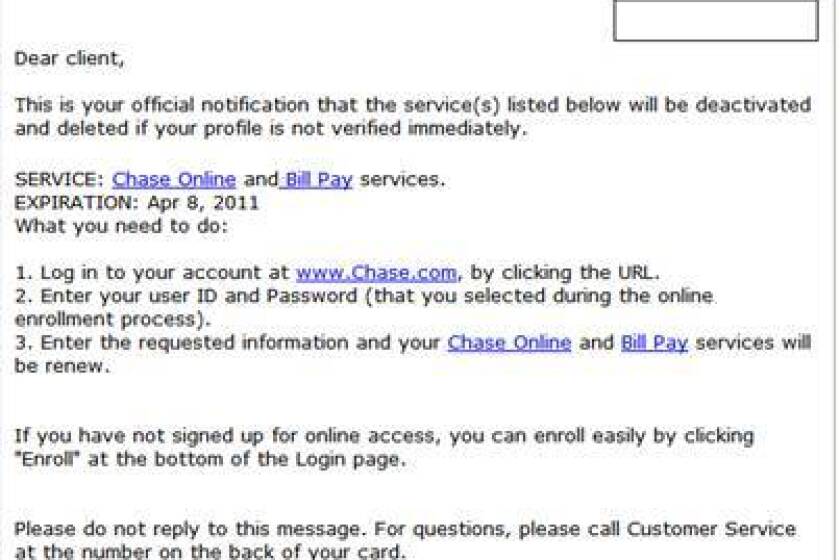
Table of Contents
The Tactics Employed in Office365 Executive Inbox Breaches
Cybercriminals employ various tactics to breach Office365 executive inboxes, often combining multiple methods for maximum impact. Understanding these tactics is the first step in effective defense.
Phishing and Spear Phishing Attacks
These remain the most prevalent entry points for Office365 security breaches. Attackers craft highly convincing emails designed to trick executives into revealing credentials or clicking malicious links. These attacks are highly effective because they often leverage:
- Use of personalized details for increased credibility: Attackers research their targets, incorporating specific details about the company, individuals, and ongoing projects to build trust and bypass suspicion.
- Exploitation of known vulnerabilities in Office365 applications: Attackers may exploit known weaknesses in Office365 applications or integrations to deliver malware or gain unauthorized access. Staying updated with security patches is crucial.
- Sophisticated email spoofing techniques to mimic trusted senders: Attackers use techniques to forge sender addresses, making emails appear to originate from legitimate sources like internal colleagues or trusted business partners. This makes them difficult to distinguish from genuine communications.
Credential Stuffing and Brute-Force Attacks
Attackers frequently utilize stolen credentials obtained from other breaches or employ automated tools to try various password combinations. This is particularly effective when:
- Compromised password databases are readily available on the dark web: Stolen credentials are often sold on the dark web, providing attackers with a readily available pool of usernames and passwords to try.
- Weak or reused passwords make accounts vulnerable: Using weak, easily guessable passwords or reusing the same password across multiple accounts significantly increases the risk of a successful breach.
- Lack of multi-factor authentication (MFA) significantly increases the risk: MFA adds an extra layer of security, requiring more than just a password to access an account, making it much harder for attackers to gain access even with stolen credentials.
Exploiting Zero-Day Vulnerabilities
Attackers may leverage undiscovered vulnerabilities (zero-day exploits) in Office365 software to gain unauthorized access. This necessitates:
- Immediate patching of software updates is crucial for mitigation: Regularly updating Office365 applications and operating systems patches known vulnerabilities, reducing the window of opportunity for attackers.
- Regular security audits to detect potential weaknesses: Regular security assessments can identify and address vulnerabilities before attackers can exploit them.
- Collaboration with security vendors for early threat detection: Working closely with security vendors provides access to early warnings about emerging threats and vulnerabilities.
The Devastating Impact of Office365 Breaches on Businesses
The consequences of a successful Office365 security breach can be severe and far-reaching, impacting multiple aspects of a business.
Financial Losses
Data breaches can lead to significant financial losses, including:
- Direct financial losses from theft and extortion: Attackers may steal sensitive financial data or demand ransoms for unlocking encrypted data.
- Indirect losses from reputational damage and business disruption: The disruption caused by a breach, coupled with reputational damage, can lead to significant financial losses.
- Costs associated with incident response and recovery: Responding to and recovering from a security breach involves substantial costs, including legal fees, forensic investigations, and system repairs.
Reputational Damage
A security breach can severely damage a company's reputation, resulting in:
- Negative media coverage and public scrutiny: Public disclosure of a breach can lead to negative media attention and public scrutiny, damaging the company's image.
- Loss of customer confidence and market share: Customers may lose trust in a company that has experienced a data breach, leading to a loss of business and market share.
- Damage to brand image and long-term business prospects: The long-term impact of a security breach can significantly damage a company's brand image and future prospects.
Legal and Regulatory Consequences
Companies may face legal action and substantial fines for non-compliance with data protection regulations, such as:
- Non-compliance penalties and legal fees: Failure to comply with regulations like GDPR and CCPA can result in hefty fines and legal fees.
- Investigations by regulatory bodies: Regulatory bodies may launch investigations into the breach, adding to the costs and potential penalties.
- Potential lawsuits from affected customers: Affected customers may launch lawsuits against the company for failing to protect their data.
Protecting Your Organization from Office365 Security Breaches
Proactive measures are essential to mitigate the risk of an Office365 security breach.
Implementing Robust Security Measures
Implementing a multi-layered security approach is crucial. This should include:
- Enforce strong password policies and password managers: Implement strong password policies and encourage employees to use password managers to create and manage complex passwords.
- Regular security audits and penetration testing: Conduct regular security audits and penetration testing to identify and address vulnerabilities.
- Invest in advanced security solutions like SIEM and EDR: Consider investing in advanced security solutions such as Security Information and Event Management (SIEM) and Endpoint Detection and Response (EDR) systems. These tools provide enhanced monitoring and threat detection capabilities.
Employee Training and Awareness
Educating employees is a critical component of a robust security strategy. This involves:
- Regular security awareness training programs: Conduct regular training programs to educate employees about phishing scams, social engineering tactics, and safe password practices.
- Simulate phishing attacks to test employee vigilance: Regularly simulate phishing attacks to assess employee awareness and identify vulnerabilities in your security protocols.
- Clear communication of security policies and procedures: Clearly communicate security policies and procedures to all employees and ensure they understand their responsibilities.
Proactive Monitoring and Threat Detection
Continuous monitoring and threat detection are crucial for early identification and response to potential breaches. This requires:
- Real-time threat monitoring and alerts: Implement systems that provide real-time threat monitoring and alerts, allowing for swift responses to potential breaches.
- Intrusion detection and prevention systems: Utilize intrusion detection and prevention systems to identify and block malicious activity.
- Regular security information and event management (SIEM) reviews: Regularly review SIEM logs to identify patterns and potential threats.
Conclusion
The targeting of executive inboxes in Office365 security breaches poses a significant threat to businesses of all sizes, leading to substantial financial losses and reputational damage. By understanding the tactics employed by attackers and implementing robust security measures, including employee training and proactive threat detection, organizations can significantly reduce their risk. Don't wait until it's too late. Take action now to strengthen your Office365 security and protect your valuable data and reputation from devastating Office365 security breaches. Invest in comprehensive security solutions and ongoing training to build a resilient defense against these increasingly sophisticated attacks. Proactive management of your Office365 security is not just a best practice—it's a business imperative.

Featured Posts
-
 English Language Leaders Debate 5 Crucial Economic Insights
Apr 22, 2025
English Language Leaders Debate 5 Crucial Economic Insights
Apr 22, 2025 -
 Cassidy Hutchinson Memoir A Deeper Look At The January 6th Events
Apr 22, 2025
Cassidy Hutchinson Memoir A Deeper Look At The January 6th Events
Apr 22, 2025 -
 Trade Conflicts And Their Impact On Americas Global Financial Position Under Trump
Apr 22, 2025
Trade Conflicts And Their Impact On Americas Global Financial Position Under Trump
Apr 22, 2025 -
 Post Easter Truce Russias Renewed Assault On Ukraine
Apr 22, 2025
Post Easter Truce Russias Renewed Assault On Ukraine
Apr 22, 2025 -
 Why Nike Shoe Manufacturing Remains A Challenge For Robots
Apr 22, 2025
Why Nike Shoe Manufacturing Remains A Challenge For Robots
Apr 22, 2025
Latest Posts
-
 Chicago Bulls And New York Knicks Injury Updates Whos Playing
May 12, 2025
Chicago Bulls And New York Knicks Injury Updates Whos Playing
May 12, 2025 -
 Ny Knicks Vs Cleveland Cavaliers Where To Watch Tv Channel And Live Stream
May 12, 2025
Ny Knicks Vs Cleveland Cavaliers Where To Watch Tv Channel And Live Stream
May 12, 2025 -
 Chicago Bulls Vs New York Knicks Latest Injury Reports
May 12, 2025
Chicago Bulls Vs New York Knicks Latest Injury Reports
May 12, 2025 -
 Nba Knicks Vs Bulls Game Predictions Odds Comparison And Best Bets 2 20 2025
May 12, 2025
Nba Knicks Vs Bulls Game Predictions Odds Comparison And Best Bets 2 20 2025
May 12, 2025 -
 Bet365 Bonus Code Nypbet Expert Picks And Odds For Knicks Vs Pistons
May 12, 2025
Bet365 Bonus Code Nypbet Expert Picks And Odds For Knicks Vs Pistons
May 12, 2025
