Execs' Office365 Accounts Breached: Millions Made, Feds Say

Table of Contents
The Scale and Impact of the Office365 Breach
The impact of this Office365 security breach extends far beyond the immediate financial losses. The reported millions of dollars in financial fraud represent just the tip of the iceberg. The consequences are multifaceted and far-reaching:
-
Massive Financial Losses: The sheer amount of money lost underscores the effectiveness of the attack and the potential for significant financial damage from an Office365 account takeover. This loss isn't limited to direct theft; it includes costs associated with investigation, remediation, and reputational repair.
-
Severe Reputational Damage: A data breach of this magnitude can severely damage a company's reputation, eroding trust among clients, partners, and investors. The negative publicity can lead to lost business and long-term financial instability. The consequences of a compromised reputation can be as damaging, if not more so, than the direct financial losses.
-
Exposure of Sensitive Data: The breach exposed sensitive company data, including strategic plans, financial information, intellectual property, and potentially even personally identifiable information (PII) of employees. This sensitive data can be used for further malicious purposes, including blackmail, identity theft, and competitive espionage. The long-term consequences of data exposure can be devastating.
-
Sophisticated Multi-Stage Attack: The investigation revealed a complex, multi-stage attack, indicating a high level of sophistication on the part of the perpetrators. This suggests that simple security measures would likely have been insufficient to prevent the breach. Understanding the complexity of the attack highlights the need for robust, layered security.
-
Uncertain Number of Affected Executives: The exact number of executives whose Office365 accounts were compromised is still being determined, further highlighting the potential scope and severity of this cybersecurity incident. The ongoing investigation underscores the need for continuous monitoring and vigilance.
Methods Used in the Office365 Account Takeover
The methods employed in this Office365 account takeover showcase the ever-evolving tactics used by cybercriminals. Understanding these methods is crucial in implementing effective preventative measures:
-
Spear Phishing Campaigns: The investigation points to highly targeted spear phishing campaigns as the primary entry point. These campaigns used personalized emails designed to trick executives into revealing their credentials or clicking on malicious links. These attacks are incredibly effective because they leverage social engineering tactics.
-
Credential Stuffing: Compromised credentials obtained through phishing or other means were likely used in subsequent credential stuffing attacks to gain access to other accounts and systems. This highlights the interconnectedness of security vulnerabilities.
-
Malware Deployment: Malware may have been deployed to gain persistent access to the compromised systems, enabling the attackers to monitor activity, steal data, and maintain control over time. The persistent nature of malware makes detection and removal challenging.
-
Third-Party Application Exploitation: The attackers may have exploited vulnerabilities in third-party applications integrated with Office365, highlighting the importance of securing the entire ecosystem, not just Office365 itself. Vulnerabilities in interconnected systems represent significant security risks.
-
MFA Bypass Attempts: Circumvention of multi-factor authentication (MFA) is strongly suspected, indicating that even robust security measures can be overcome if not properly implemented and monitored. The bypass of MFA underscores the need for continuous improvement of security protocols.
Protecting Your Organization from Similar Office365 Breaches
The lessons learned from this Office365 breach emphasize the importance of proactive and layered security measures. Organizations must take immediate action to protect themselves:
-
Robust Multi-Factor Authentication (MFA): Implement strong MFA for all Office365 accounts. This adds an extra layer of security, making it significantly harder for attackers to gain access even if they obtain passwords.
-
Comprehensive Cybersecurity Awareness Training: Provide regular and engaging cybersecurity awareness training for all employees, focusing on phishing and social engineering tactics. Employees are often the weakest link in security; training empowers them to identify and report suspicious activity.
-
Regular Updates and Patches: Regularly update and patch Office365 and all related applications to address known vulnerabilities. Keeping software up-to-date is a fundamental aspect of cybersecurity.
-
Advanced Threat Detection and SIEM Tools: Utilize advanced threat detection and security information and event management (SIEM) tools to monitor for suspicious activity and promptly identify potential breaches. Early detection is crucial for minimizing damage.
-
Comprehensive Incident Response Plan: Develop and regularly test a comprehensive incident response plan to ensure a coordinated and effective response in the event of a security breach. A well-defined plan minimizes the impact of a breach.
-
Robust Access Control and Least Privilege: Implement robust access control and least privilege policies, limiting access to sensitive data and systems only to those who absolutely need it. Restricting access reduces the potential impact of a compromise.
Conclusion
The Office365 breach affecting executive accounts demonstrates the ever-evolving nature of cyber threats and the critical need for proactive security measures. The financial and reputational consequences of such attacks can be devastating. Don't become another statistic. Strengthen your Office365 security today by implementing robust security measures, educating your employees, and investing in advanced threat detection tools. Protect your organization and your executives from the devastating impact of an Office365 breach. Learn more about comprehensive Office365 security solutions now.

Featured Posts
-
 Human Centered Ai An Interview With Microsofts Design Chief
Apr 26, 2025
Human Centered Ai An Interview With Microsofts Design Chief
Apr 26, 2025 -
 Access To Birth Control The Impact Of Over The Counter Availability Post Roe
Apr 26, 2025
Access To Birth Control The Impact Of Over The Counter Availability Post Roe
Apr 26, 2025 -
 Ryujinx Emulator Development Halted Official Statement Following Nintendo Contact
Apr 26, 2025
Ryujinx Emulator Development Halted Official Statement Following Nintendo Contact
Apr 26, 2025 -
 The Next Fed Chair Inherits A Trump Made Mess
Apr 26, 2025
The Next Fed Chair Inherits A Trump Made Mess
Apr 26, 2025 -
 Metas Future Under The Shadow Of The Trump Administration
Apr 26, 2025
Metas Future Under The Shadow Of The Trump Administration
Apr 26, 2025
Latest Posts
-
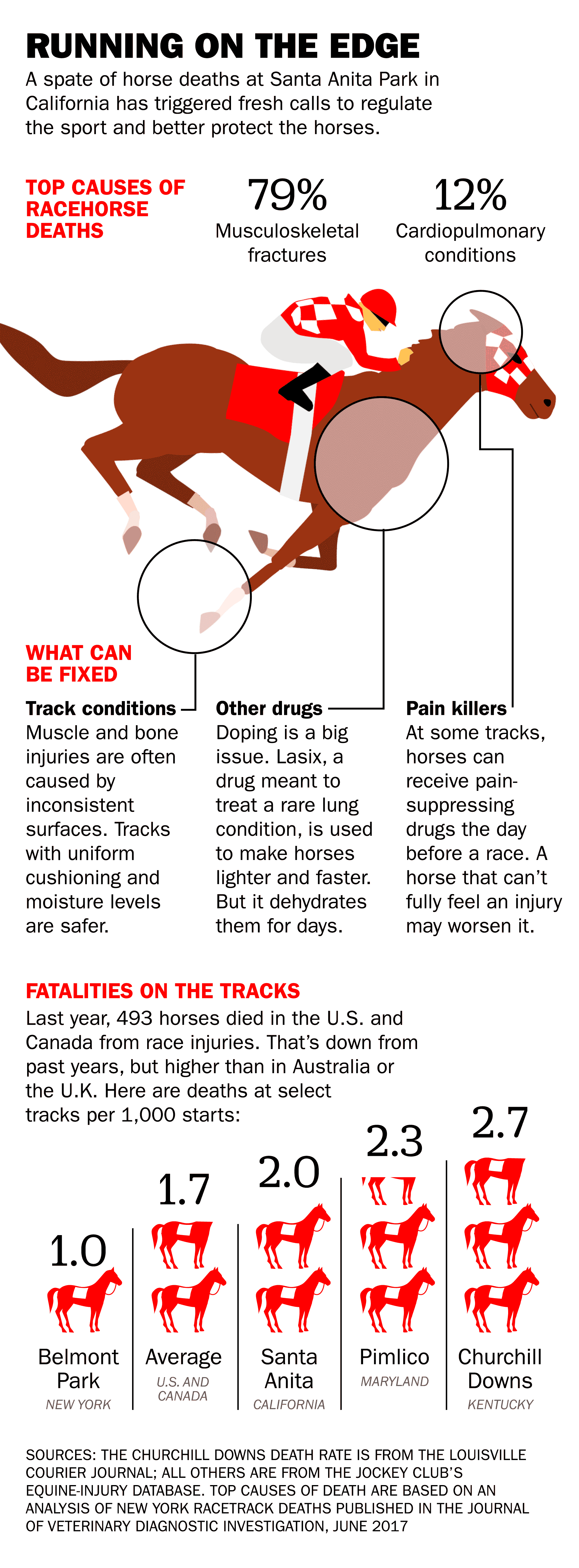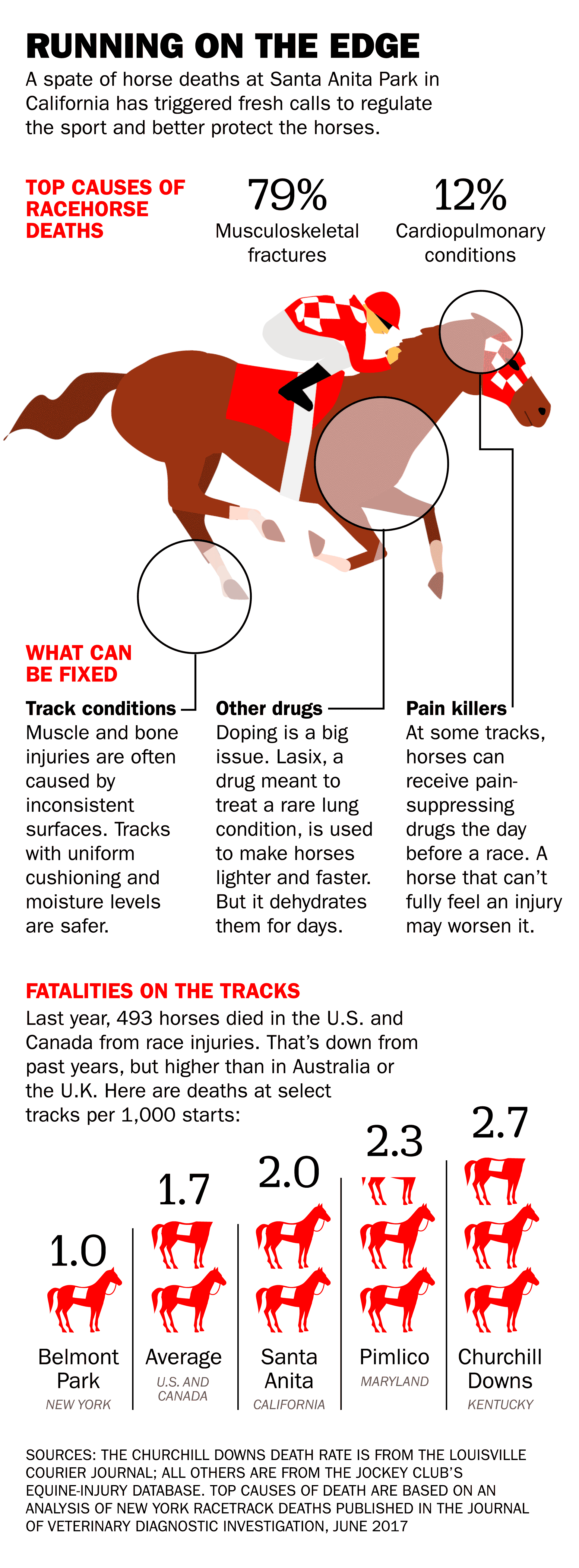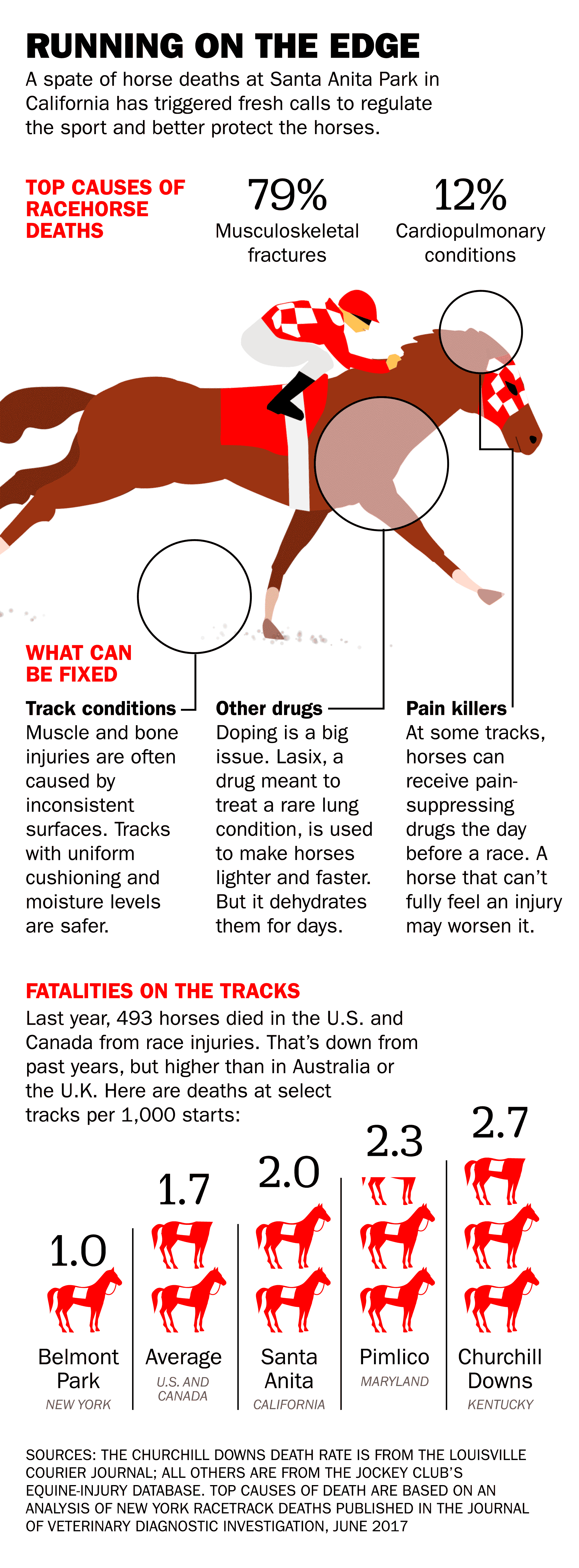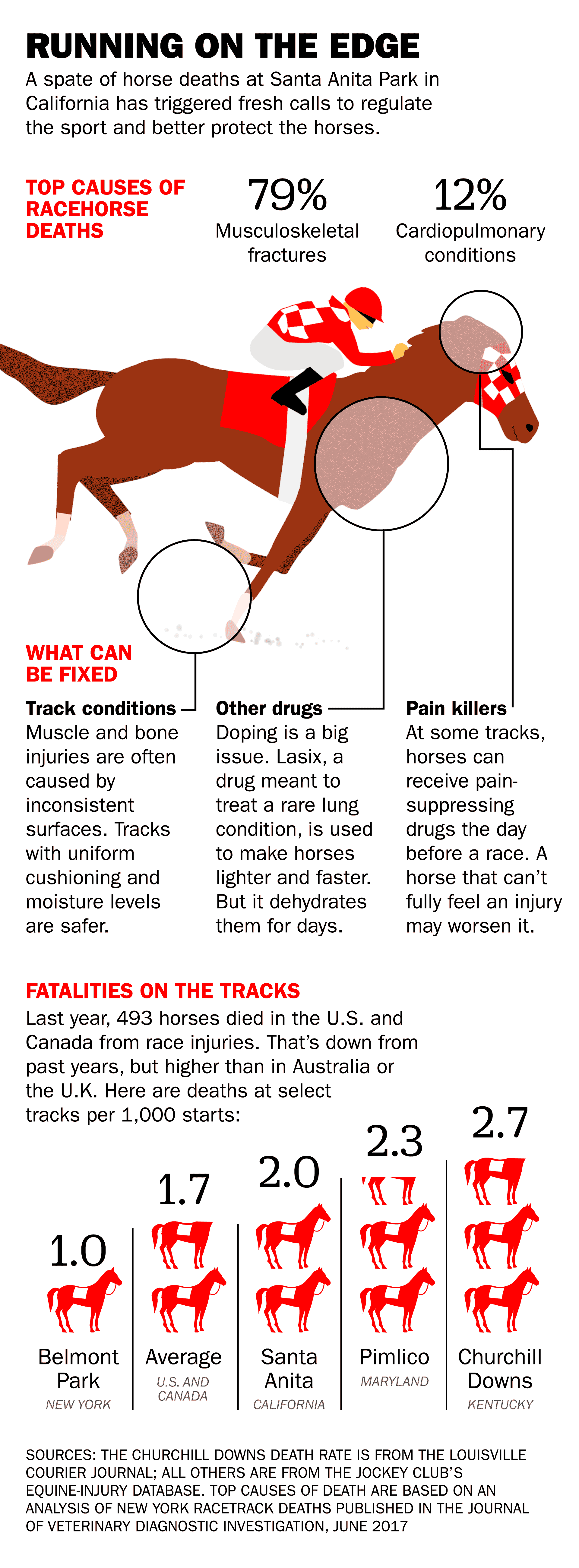 Grand National Horse Deaths A Look At The Statistics Before 2025
Apr 27, 2025
Grand National Horse Deaths A Look At The Statistics Before 2025
Apr 27, 2025 -
 Your Guide To The Grand National 2025 Runners At Aintree
Apr 27, 2025
Your Guide To The Grand National 2025 Runners At Aintree
Apr 27, 2025 -
 Grand National 2025 Key Runners And Aintree Race Preview
Apr 27, 2025
Grand National 2025 Key Runners And Aintree Race Preview
Apr 27, 2025 -
 Aintree Grand National 2025 Runners Analysis And Predictions
Apr 27, 2025
Aintree Grand National 2025 Runners Analysis And Predictions
Apr 27, 2025 -
 Vancouver Whitecaps And Pne In Stadium Construction Talks
Apr 27, 2025
Vancouver Whitecaps And Pne In Stadium Construction Talks
Apr 27, 2025
