FBI Investigation Uncovers Millions In Losses From Executive Office365 Hacks
Table of Contents
The Scale of the Problem: Financial Losses from Office 365 Breaches
The magnitude of financial losses resulting from Office 365 breaches is staggering. While the FBI hasn't released precise figures publicly for this specific investigation, similar reports indicate losses reaching millions of dollars per incident. Thousands of businesses are impacted annually, facing significant financial repercussions. The sheer volume of these incidents underscores the urgent need for robust cybersecurity strategies.
Magnitude of Financial Losses:
- Lost Revenue: Compromised accounts can disrupt operations, leading to lost sales and project delays, resulting in substantial revenue loss.
- Legal Fees and Fines: Data breaches often trigger investigations and lawsuits, leading to significant legal fees and potential fines for non-compliance with regulations like GDPR.
- Remediation Costs: Restoring compromised systems, conducting forensic investigations, and notifying affected parties can incur substantial costs.
- Reputational Damage: A data breach can severely damage a company's reputation, leading to loss of customer trust and potential long-term financial consequences. The impact on investor confidence can also result in a decrease in stock value.
Common Tactics Used in Executive Office 365 Hacks
Cybercriminals employ increasingly sophisticated tactics to target executive accounts within Office 365 environments. These attacks leverage the perceived trust associated with high-ranking individuals and exploit vulnerabilities in the platform.
Phishing and Spear Phishing Attacks:
Phishing attacks are a major vector for Office 365 breaches. Attackers send deceptive emails designed to trick recipients into revealing sensitive information, such as login credentials or downloading malicious attachments. Spear phishing attacks are even more targeted, crafting emails that appear to originate from known contacts or organizations, thereby increasing the likelihood of success.
- Examples: Emails mimicking internal communications, requests for urgent financial transactions, or notifications regarding account issues are common spear-phishing techniques.
- Exploitation of Vulnerabilities: Attackers may exploit vulnerabilities in Office 365's integrations with other applications or leverage social engineering to gain access to accounts.
- Malicious Links and Attachments: These can deliver malware or redirect users to fake login pages designed to steal credentials.
Credential Stuffing and Brute-Force Attacks:
These attacks exploit weak passwords and leverage stolen credentials from other data breaches. Credential stuffing uses lists of known usernames and passwords to try gaining access, while brute-force attacks systematically try different combinations until they find the correct password.
- Importance of Strong Passwords: Using long, complex passwords that are unique to each account significantly reduces the risk of successful attacks.
- Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring multiple forms of authentication, making it far more difficult for attackers to gain access even if they obtain a password.
- Password Management Best Practices: Utilizing a password manager to generate and securely store strong, unique passwords for each account is crucial.
Protecting Your Organization from Office 365 Hacks
Protecting your organization from Office 365 hacks requires a multi-layered approach combining robust security measures and comprehensive incident response planning.
Implementing Robust Security Measures:
- Multi-Factor Authentication (MFA): Mandatory MFA for all users is paramount, significantly reducing the success rate of credential-based attacks.
- Security Awareness Training: Regular training programs educate employees about phishing scams, social engineering tactics, and secure password practices.
- Strong Password Policies: Enforce strong password policies that mandate complexity, length, and regular password changes.
- Up-to-Date Software and Security Patches: Regularly update all software and applications, including Office 365, to patch known vulnerabilities.
- Regular Security Audits and Penetration Testing: Conduct regular security audits and penetration testing to identify and address potential weaknesses in your security posture.
The Importance of Incident Response Planning:
Having a well-defined incident response plan is vital for minimizing the impact of a successful breach.
- Steps to Take if a Breach Occurs: Establish clear procedures for containment, eradication, recovery, and communication during a cybersecurity incident.
- Involving Cybersecurity Professionals: Engage with experienced cybersecurity professionals to conduct a thorough investigation, remediate the breach, and help restore operations.
- Data Recovery and Business Continuity Strategies: Implement robust data backup and recovery procedures, and develop a business continuity plan to minimize disruption.
Conclusion
The FBI investigation into Office 365 hacks underscores the significant financial and reputational risks associated with these breaches. The substantial losses incurred highlight the urgent need for organizations to strengthen their cybersecurity defenses. Executive Office 365 accounts are prime targets, and sophisticated attacks like phishing and credential stuffing pose a constant threat. By implementing robust security measures, including multi-factor authentication, regular security awareness training, and comprehensive incident response planning, businesses can significantly reduce their vulnerability to these costly attacks. Don't become another victim of Office 365 hacks. Invest in comprehensive cybersecurity solutions and strengthen your Office 365 security today. Learn more about protecting your business from executive Office 365 breaches and safeguard your organization's future.

Featured Posts
-
 The Countrys Hottest New Business Locations A Geographic Analysis
Apr 22, 2025
The Countrys Hottest New Business Locations A Geographic Analysis
Apr 22, 2025 -
 Controversy Erupts Hegseth Signal Chat And Pentagon Disarray
Apr 22, 2025
Controversy Erupts Hegseth Signal Chat And Pentagon Disarray
Apr 22, 2025 -
 Joint Effort South Sudan And Us Government On Deportees Repatriation
Apr 22, 2025
Joint Effort South Sudan And Us Government On Deportees Repatriation
Apr 22, 2025 -
 Ftc Launches Investigation Into Open Ai And Chat Gpt
Apr 22, 2025
Ftc Launches Investigation Into Open Ai And Chat Gpt
Apr 22, 2025 -
 Understanding Stock Market Valuations Bof As Rationale For Investor Confidence
Apr 22, 2025
Understanding Stock Market Valuations Bof As Rationale For Investor Confidence
Apr 22, 2025
Latest Posts
-
 Understanding The Geographic Distribution Of New Business Hotspots
May 12, 2025
Understanding The Geographic Distribution Of New Business Hotspots
May 12, 2025 -
 Analyzing Trumps Stance On Cheap Oil And Its Effect On The Us Energy Landscape
May 12, 2025
Analyzing Trumps Stance On Cheap Oil And Its Effect On The Us Energy Landscape
May 12, 2025 -
 The Aftermath Of La Fires Accusations Of Landlord Price Gouging
May 12, 2025
The Aftermath Of La Fires Accusations Of Landlord Price Gouging
May 12, 2025 -
 A Comprehensive Map Of The Countrys Rising Business Centers
May 12, 2025
A Comprehensive Map Of The Countrys Rising Business Centers
May 12, 2025 -
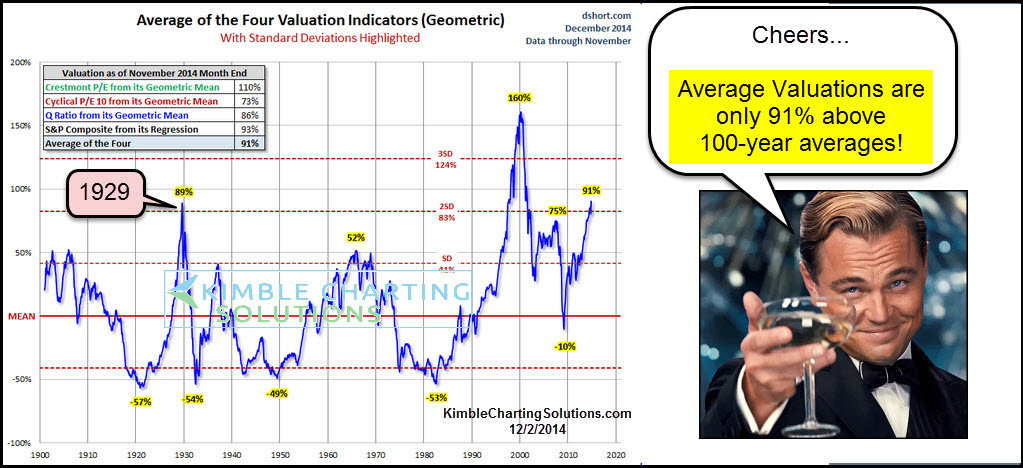 Investor Guide Bof As Assessment Of Current Stock Market Valuations
May 12, 2025
Investor Guide Bof As Assessment Of Current Stock Market Valuations
May 12, 2025
