Federal Charges: Crook Made Millions From Executive Office365 Account Hacks
Table of Contents
The Modus Operandi Behind the Office 365 Account Hacks
This section details the likely methods used by the perpetrator to breach Office 365 accounts, highlighting the sophisticated techniques employed to gain unauthorized access.
Phishing and Social Engineering
The perpetrator likely employed sophisticated phishing emails and social engineering tactics to gain access to credentials. These attacks prey on human error, exploiting trust and exploiting weaknesses in security awareness.
- Examples of phishing emails: Emails disguised as legitimate communications from reputable sources, often containing urgent requests or threats to create a sense of urgency. These might mimic internal communications or requests from known vendors.
- Successful social engineering techniques: Building rapport with targets, gaining their trust, and exploiting their desire to help or comply with perceived authority figures. This could involve pretexting, where the attacker creates a false scenario to gain information.
- Targeting of high-level executives: Executives are often targeted because they may have access to sensitive financial information and greater authority to authorize transactions.
Exploiting Software Vulnerabilities
Exploiting known vulnerabilities in Office 365 or related software is another potential attack vector. Keeping software up-to-date is crucial in mitigating these risks.
- Mention specific vulnerabilities (if known): While specific vulnerabilities in this case may not be publicly available, unpatched software often contains security flaws that cybercriminals can exploit. Zero-day exploits, vulnerabilities unknown to the software vendor, are a particularly dangerous threat.
- The importance of patching and software updates: Regularly applying security patches and updates is crucial for preventing attackers from exploiting known weaknesses. This should be a prioritized and automated process.
Credential Stuffing and Brute-Force Attacks
Stolen credentials from other platforms or brute-force attacks were likely used to gain unauthorized access to Office 365 accounts.
- How these methods work: Credential stuffing uses lists of stolen usernames and passwords obtained from other data breaches, attempting to use them across multiple platforms. Brute-force attacks try various password combinations until they find the correct one.
- Their effectiveness against Office 365: While Microsoft employs robust security measures, insufficient password complexity or the reuse of passwords across multiple accounts makes these methods effective.
The Financial Ramifications of the Office 365 Account Hacks
The financial losses caused by this hack were substantial, impacting not only the immediate financial losses but also long-term business stability.
Millions Lost Through Wire Transfers and Fraudulent Transactions
The attacker likely used wire transfers and fraudulent invoices to steal millions of dollars.
- Quantify the amount of money stolen: The indictment details the millions stolen, highlighting the scale of the financial losses.
- Mention the impact on victims' businesses: The stolen funds could have severely hampered business operations, impacting growth, and even threatening the solvency of smaller businesses.
Reputational Damage and Loss of Client Trust
Beyond direct financial losses, reputational damage and loss of client trust are significant consequences of such breaches.
- Explain the potential consequences of data breaches for a company's reputation and client relationships: A data breach can erode public trust, leading to loss of customers, decreased investor confidence, and potential legal ramifications. This damage can be long-lasting.
Strengthening Your Office 365 Security: Preventative Measures
Proactive measures are crucial to safeguarding your business from similar Office 365 account hacks.
Multi-Factor Authentication (MFA): An Essential First Step
Implementing MFA is a critical first step in preventing unauthorized access.
- Explain how MFA works: MFA adds an extra layer of security by requiring multiple forms of authentication, such as a password and a verification code from a mobile device.
- Its benefits in preventing account hacks: Even if an attacker obtains a password, they will be unable to access the account without the second authentication factor.
Robust Password Policies and Employee Training
Strong passwords and comprehensive security awareness training are essential components of a robust security strategy.
- Suggest best practices for password management: Enforce strong, unique passwords, encourage the use of password managers, and implement regular password rotation policies.
- Topics to cover in security training: Phishing awareness, social engineering tactics, password security, and safe browsing habits should all be addressed in employee training programs.
Regular Security Audits and Vulnerability Assessments
Proactive identification and addressing of vulnerabilities are critical for maintaining a strong security posture.
- Recommend types of security audits and assessments: Regular penetration testing, vulnerability scans, and security audits help identify weaknesses in your system.
- Frequency of checks: Regular security audits and assessments should be conducted at least annually, or more frequently depending on the sensitivity of the data handled.
Conclusion
This case of a crook making millions from Office 365 account hacks serves as a stark warning. The financial and reputational repercussions of such breaches can be devastating. By implementing robust security measures like multi-factor authentication, strong password policies, employee training, and regular security audits, organizations can significantly reduce their vulnerability to Office 365 account hacks and other cyber threats. Don't wait for a similar disaster – take proactive steps today to strengthen your Office 365 security and protect your valuable data and financial assets. Invest in robust Office 365 security practices now, before it’s too late.

Featured Posts
-
 Kai Cenat Under Fire After Friends Racist Comments The Silence Speaks Volumes
May 27, 2025
Kai Cenat Under Fire After Friends Racist Comments The Silence Speaks Volumes
May 27, 2025 -
 Does An Angry Elon Musk Benefit Tesla
May 27, 2025
Does An Angry Elon Musk Benefit Tesla
May 27, 2025 -
 Analiza Parerilor Influenta Politicii In Viziunea Lui Mirel Curea
May 27, 2025
Analiza Parerilor Influenta Politicii In Viziunea Lui Mirel Curea
May 27, 2025 -
 Watch Tracker Season 2 Episode 15 The Grey Goose Preview
May 27, 2025
Watch Tracker Season 2 Episode 15 The Grey Goose Preview
May 27, 2025 -
 Janet Jacksons Style Evolution A Nostalgic Journey Through Her Iconic Looks
May 27, 2025
Janet Jacksons Style Evolution A Nostalgic Journey Through Her Iconic Looks
May 27, 2025
Latest Posts
-
 Elon Musks Family Wealth The Reality Behind The Billions Maye Musks Account
May 30, 2025
Elon Musks Family Wealth The Reality Behind The Billions Maye Musks Account
May 30, 2025 -
 Understanding Elon Musks Familys Financial Journey Maye Musks Perspective
May 30, 2025
Understanding Elon Musks Familys Financial Journey Maye Musks Perspective
May 30, 2025 -
 Elon Musks Alleged Paternity Of Amber Heards Twins A Deeper Look
May 30, 2025
Elon Musks Alleged Paternity Of Amber Heards Twins A Deeper Look
May 30, 2025 -
 Maye Musk On Elon Musks Wealth Years Of Hardship Before Success
May 30, 2025
Maye Musk On Elon Musks Wealth Years Of Hardship Before Success
May 30, 2025 -
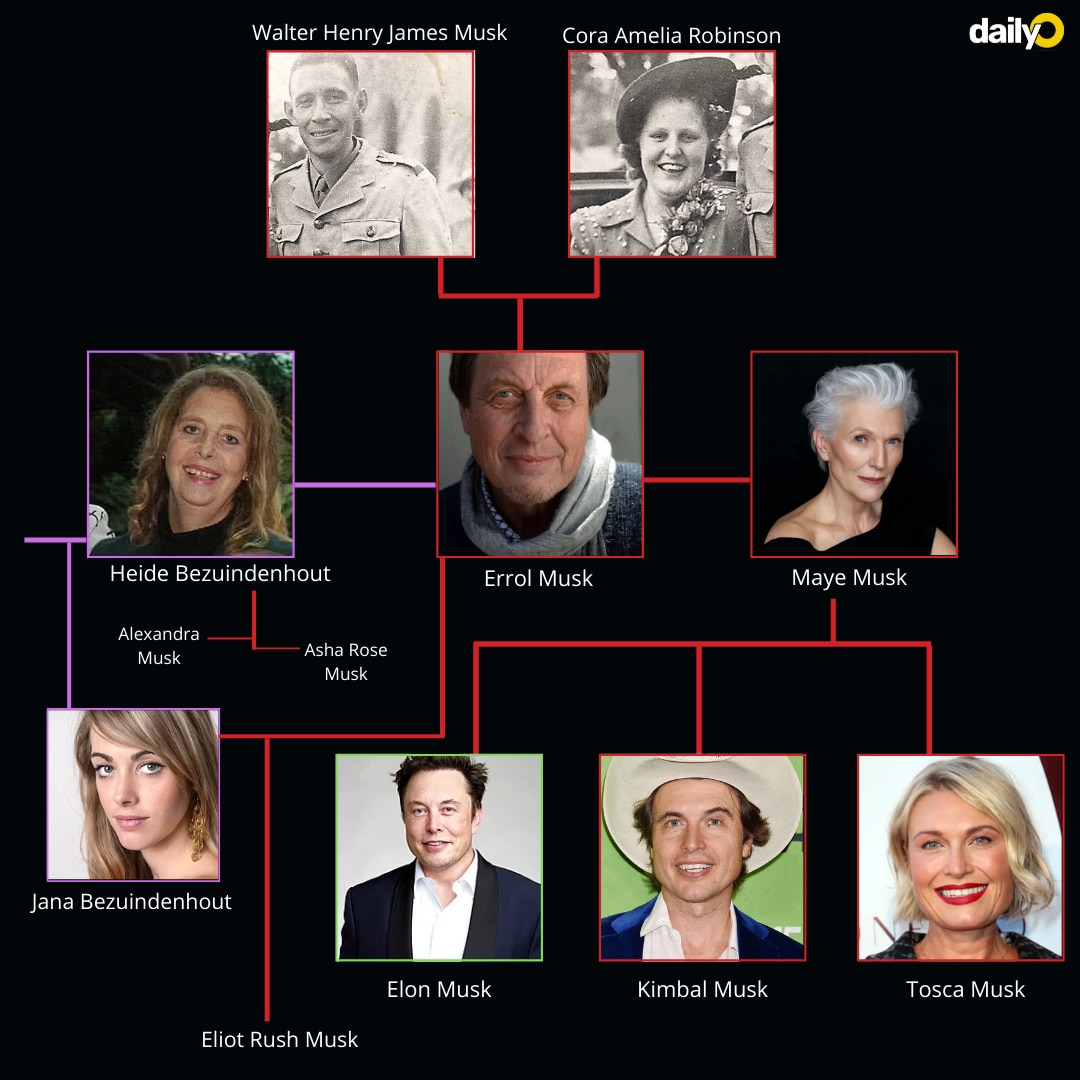 The Truth About Elon Musks Family Fortune A Look At Maye Musks Journey
May 30, 2025
The Truth About Elon Musks Family Fortune A Look At Maye Musks Journey
May 30, 2025
