Millions Stolen Through Executive Office365 Account Compromise
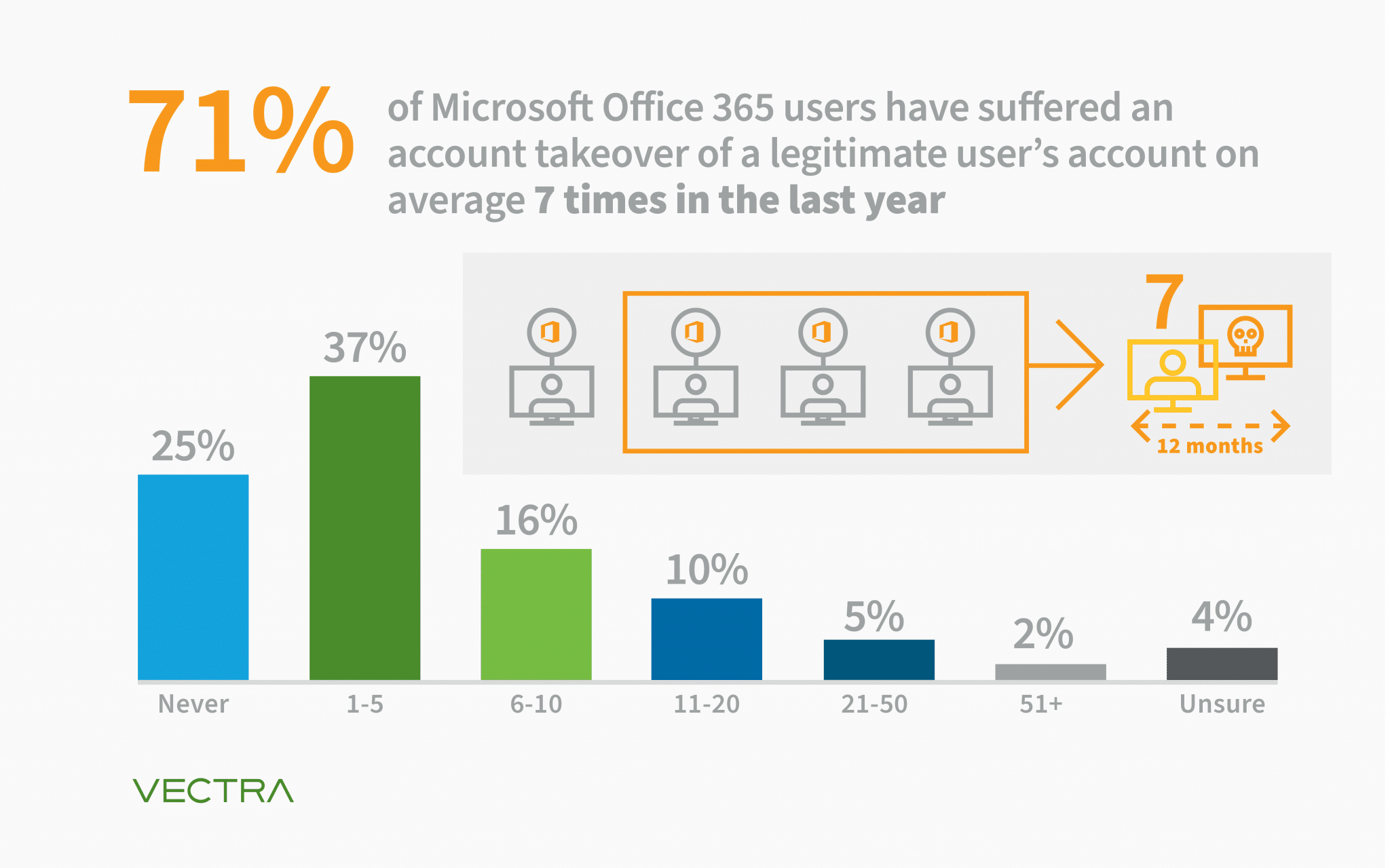
Table of Contents
A staggering $2.4 million was lost last year by a single company due to an Executive Office365 account compromise. This shocking statistic highlights the escalating threat of cyberattacks targeting high-level executives and their access to sensitive company data. The implications of an Office 365 security breach, specifically targeting executive accounts, are devastating, involving significant financial losses, reputational damage, and legal ramifications. This article will shed light on the sophisticated methods used in these attacks, the devastating consequences, and crucial preventative measures to safeguard your organization from executive account hacking and other cybersecurity threats. Understanding the risks associated with Executive Office365 account compromise is the first step towards robust protection.
2. Main Points:
H2: Sophisticated Phishing and Social Engineering Tactics
The success of many executive account hacking attempts relies on sophisticated phishing and social engineering techniques. Attackers meticulously craft their campaigns to exploit the trust and authority associated with executive positions.
H3: Targeted Phishing Campaigns:
Attackers employ highly personalized phishing emails and messages, often mimicking legitimate communications from trusted sources. These targeted attacks leverage social engineering to bypass security protocols.
- Spear phishing: Emails appear to come from known individuals or organizations, often containing specific details about the target's work or personal life.
- CEO fraud/Whaling: Attackers impersonate high-ranking executives to trick employees into transferring funds or revealing sensitive information.
- Pretexting: Attackers create a believable scenario to manipulate the victim into providing access or information.
These techniques often bypass traditional security measures because they are highly personalized and play on human psychology, making them exceptionally effective.
H3: Exploiting Weak Passwords and Authentication:
Weak or reused passwords are a major vulnerability in Office 365 security breach scenarios. Single-factor authentication (SFA) offers minimal protection against determined attackers.
- Strong Password Best Practices: Use a minimum of 12 characters, combining uppercase and lowercase letters, numbers, and symbols. Avoid using personal information or easily guessable words.
- Password Management Tools: Utilize password managers to generate and securely store complex passwords.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security by requiring multiple forms of verification, significantly reducing the risk of unauthorized access. This includes methods like Time-Based One-Time Passwords (TOTP), and FIDO2 security keys.
Implementing MFA is crucial for mitigating the risk of executive account hacking and securing Executive Office365 accounts.
H2: The High Cost of Executive Office365 Account Compromise
The consequences of a successful attack extend far beyond the initial breach. The financial and reputational damage can be catastrophic.
H3: Financial Losses:
The financial ramifications can be crippling.
- Wire fraud: Attackers can redirect funds to fraudulent accounts.
- Data theft: Stolen intellectual property, customer data, and confidential financial information can lead to substantial losses.
- Ransom demands: Attackers may demand payment to restore access or prevent further damage.
For example, a recent case saw a company lose over $5 million due to an Executive Office365 account compromise involving wire fraud.
H3: Reputational Damage and Legal Consequences:
The fallout from a breach goes far beyond monetary loss.
- Loss of customer trust: Damaged reputation can lead to decreased sales and customer churn.
- Investor concern: Share prices may plummet, impacting investor confidence.
- Regulatory compliance issues: Breaches can lead to significant fines under regulations like GDPR and CCPA.
- Lawsuits: Businesses can face lawsuits from customers, partners, and investors.
The legal and reputational repercussions of an Office 365 security breach can be long-lasting and extremely costly.
H2: Protecting Your Executive Office365 Accounts: Proactive Security Measures
Protecting executive accounts requires a multi-layered approach incorporating technological and human elements.
H3: Implementing Robust Multi-Factor Authentication (MFA):
MFA is non-negotiable.
- Time-Based One-Time Passwords (TOTP): Generate unique codes using an authenticator app.
- FIDO2 Security Keys: Hardware security keys provide strong authentication.
- Microsoft Authenticator App: Use Microsoft's own app for seamless integration with Office 365.
Enforce MFA for all executive accounts to significantly reduce the risk of unauthorized access.
H3: Security Awareness Training for Executives:
Educating executives about phishing techniques and best practices is crucial.
- Regular phishing simulations: Test employees' ability to identify malicious emails.
- Interactive training modules: Engage executives with engaging content.
- Emphasis on social engineering tactics: Train executives to recognize and report suspicious communications.
Invest in comprehensive security awareness training programs to build a culture of cybersecurity.
H3: Advanced Threat Protection and Security Information and Event Management (SIEM):
Advanced security solutions provide an extra layer of defense.
- Microsoft Defender for Office 365: Offers advanced threat protection features.
- Security Information and Event Management (SIEM) systems: Monitor security events and detect anomalies.
These tools can help detect and respond to threats in real-time, minimizing the impact of a successful breach.
3. Conclusion: Safeguarding Your Organization from Executive Office365 Account Compromise
The threat of Executive Office365 account compromise is real and the consequences severe. From sophisticated phishing attacks exploiting human psychology to the devastating financial and reputational damage, the risks are substantial. However, by implementing robust MFA, conducting regular security awareness training for executives, and leveraging advanced threat protection solutions, organizations can significantly reduce their vulnerability. Don't wait until it's too late. Secure Your Executive Office365 Accounts Today! Take immediate action to protect your business from the devastating effects of Executive Office365 Account Compromise. Learn more about preventing Executive Office365 account breaches by exploring resources on advanced security measures and implementing a comprehensive cybersecurity strategy. Protect your organization and its valuable assets.

Featured Posts
-
 Addressing Criticism Lizzos Trainer Speaks Out On Her Fitness Journey
May 04, 2025
Addressing Criticism Lizzos Trainer Speaks Out On Her Fitness Journey
May 04, 2025 -
 Ufc 314 Winners Losers And Key Moments From Volkanovski Vs Lopes
May 04, 2025
Ufc 314 Winners Losers And Key Moments From Volkanovski Vs Lopes
May 04, 2025 -
 Investor Guide Bof As View On High Stock Market Valuations
May 04, 2025
Investor Guide Bof As View On High Stock Market Valuations
May 04, 2025 -
 Ai Driven Podcast Creation Processing Repetitive Documents For Profound Insights
May 04, 2025
Ai Driven Podcast Creation Processing Repetitive Documents For Profound Insights
May 04, 2025 -
 Nhl Playoff Matchups Predicting The Stanley Cup Champion
May 04, 2025
Nhl Playoff Matchups Predicting The Stanley Cup Champion
May 04, 2025
Latest Posts
-
 Emma Stooyn To Forema Poy Allakse Ta Panta
May 04, 2025
Emma Stooyn To Forema Poy Allakse Ta Panta
May 04, 2025 -
 I Anatreptiki Emfanisi Tis Emma Stooyn Leptomereies Gia To Forema
May 04, 2025
I Anatreptiki Emfanisi Tis Emma Stooyn Leptomereies Gia To Forema
May 04, 2025 -
 Emma Stoun U Minispidnitsi Foto Z Premiyi Shou Biznes
May 04, 2025
Emma Stoun U Minispidnitsi Foto Z Premiyi Shou Biznes
May 04, 2025 -
 Emma Stooyn I Anatreptiki Epilogi Forematos Se Prosfati Ekdilosi
May 04, 2025
Emma Stooyn I Anatreptiki Epilogi Forematos Se Prosfati Ekdilosi
May 04, 2025 -
 I Emma Stooyn Mia Apisteyti Emfanisi Me To Forema Tis
May 04, 2025
I Emma Stooyn Mia Apisteyti Emfanisi Me To Forema Tis
May 04, 2025
