Office365 Executive Inbox Compromise Leads To Multi-Million Dollar Theft
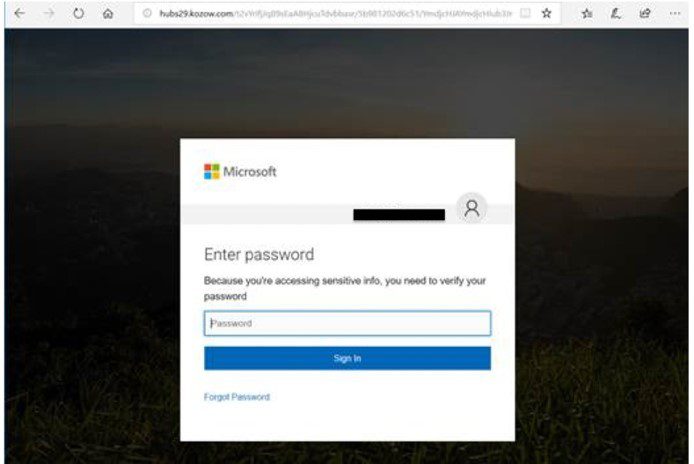
Table of Contents
The Anatomy of the Office365 Executive Inbox Compromise
The successful compromise of an executive's Office365 inbox often involves a combination of technical expertise and social engineering. Attackers employ various methods, aiming for the least resistant path. These methods exploit vulnerabilities within Office365 itself or leverage human error.
-
Spear Phishing: Highly targeted phishing emails are crafted to mimic legitimate communications from trusted sources—colleagues, clients, or vendors. These emails often contain urgent requests or sensitive information to pressure the recipient into immediate action.
-
Weak Passwords & Lack of MFA: Many organizations still struggle with enforcing strong password policies and mandating multi-factor authentication (MFA). This creates a significant vulnerability, as weak passwords are easily cracked, and MFA provides an extra layer of security to prevent unauthorized access even if credentials are compromised.
-
Malicious Links & Attachments: Emails containing malicious links or attachments can deliver malware directly to the victim's computer, granting attackers access to the system and potentially the Office365 account. This malware can range from keyloggers recording keystrokes to sophisticated backdoors allowing remote control of the system.
-
Credential Stuffing: Attackers utilize lists of stolen credentials obtained from previous data breaches, attempting to log into accounts using these combinations. This is particularly effective against accounts with weak or reused passwords.
Social engineering plays a critical role. Attackers spend time researching their targets, building a profile to understand their communication style and create convincing phishing emails. The goal is to build trust and manipulate the executive into taking the desired action, often under pressure or without proper verification.
The Financial Ramifications of the Data Breach
The consequences of a successful Office365 executive inbox compromise can be catastrophic. In the case study we are examining (details omitted for confidentiality reasons), the financial losses exceeded several million dollars.
-
Wire Transfers: Attackers often target the organization's payment systems, diverting funds through fraudulent wire transfers to accounts they control. This is often done by manipulating invoice details or creating fake invoices.
-
Invoice Fraud: Attackers might intercept legitimate invoices, altering payment details to redirect funds to their accounts. This requires access to email communication and a deep understanding of the organization's financial processes.
-
Loss of Sensitive Intellectual Property: The compromised inbox may contain valuable intellectual property, trade secrets, or sensitive client data. The theft of this information can result in significant financial losses and reputational damage.
-
Reputational Damage & Loss of Customer Trust: A data breach, especially one involving financial loss, severely impacts an organization's reputation. Customers may lose trust, leading to decreased sales and long-term financial damage.
Beyond direct financial losses, the organization faces indirect costs such as legal fees, forensic investigations, remediation efforts, and the cost of restoring damaged systems and data. These hidden costs often significantly inflate the overall financial impact of the breach.
Lessons Learned and Best Practices for Preventing Office365 Executive Inbox Compromise
Preventing Office365 executive inbox compromises requires a multi-layered approach combining technical security measures with robust employee training.
-
Strong Password Policies & MFA: Enforce strong password policies that require complex passwords and regular changes. Mandate multi-factor authentication (MFA) for all users, especially executives.
-
Security Awareness Training: Regularly train employees, particularly executives, on identifying and avoiding phishing attempts and social engineering tactics. Simulate phishing attacks to assess employee vulnerability and refine training programs.
-
Advanced Threat Protection: Utilize the advanced threat protection features built into Office365, including anti-malware, anti-phishing, and anti-spam capabilities.
-
Security Audits & Penetration Testing: Regularly conduct security audits and penetration testing to identify vulnerabilities in your systems and processes. This proactive approach helps uncover weaknesses before attackers can exploit them.
-
Email Authentication Protocols (SPF, DKIM, DMARC): Implementing these protocols helps validate the authenticity of emails, reducing the likelihood of spoofing attacks.
-
Robust Financial Controls: Establish clear financial control protocols and verification procedures for all payments, especially large wire transfers. Implement multiple layers of authorization to prevent unauthorized transactions.
The Importance of Incident Response Planning
Having a well-defined incident response plan is critical in mitigating the damage from a successful attack. This plan should outline clear communication protocols, containment strategies, and steps for recovering from the breach. A rapid and effective response can minimize financial losses and reputational damage. Regular drills and simulations are essential to ensure the plan’s effectiveness.
Conclusion: Protecting Your Organization from Office365 Executive Inbox Compromise
The case study highlights the devastating consequences of compromised executive inboxes, demonstrating the critical need for proactive security measures. Attack vectors are diverse, from sophisticated phishing techniques to exploiting weak passwords and lack of MFA. Protecting your organization requires a comprehensive strategy encompassing strong password policies, mandatory MFA, regular security awareness training, robust email authentication, advanced threat protection within Office365, and rigorous incident response planning. Don't wait for a multi-million dollar loss—assess your current Office365 security posture today. Implement the best practices outlined above and invest in advanced security solutions to safeguard your organization against Office365 executive inbox compromise. Consider conducting a security assessment or implementing employee cybersecurity training programs to further strengthen your defenses. Protecting your executives and your bottom line starts now.

Featured Posts
-
 Pete Hegseth And The Trump Platform Controversy And Communication
Apr 24, 2025
Pete Hegseth And The Trump Platform Controversy And Communication
Apr 24, 2025 -
 The Bold And The Beautiful February 20th Spoilers Steffy Liam And Finn
Apr 24, 2025
The Bold And The Beautiful February 20th Spoilers Steffy Liam And Finn
Apr 24, 2025 -
 Bof A On Stock Market Valuations Addressing Investor Concerns
Apr 24, 2025
Bof A On Stock Market Valuations Addressing Investor Concerns
Apr 24, 2025 -
 Are High Stock Market Valuations Justified Bof As Analysis For Investors
Apr 24, 2025
Are High Stock Market Valuations Justified Bof As Analysis For Investors
Apr 24, 2025 -
 Cassidy Hutchinson Jan 6 Testimony And Upcoming Memoir
Apr 24, 2025
Cassidy Hutchinson Jan 6 Testimony And Upcoming Memoir
Apr 24, 2025
